
by Doug Kreitzberg | Dec 16, 2020 | Behavior, Cybersecurity, Privacy
In recent years, much has been made of the privacy paradox: the idea that, while people say they value their privacy, their online behaviors show they are more willing to give away personal information than they’d like to think. Tech giants like Facebook and Google have faced a number of highly public privacy standards, yet millions upon millions of users continue to use these services every day. However, what happens when we think of the value of privacy not in terms of how much we want to protect our privacy, but instead in terms of much we are willing to spend to keep our data private. Newly published research does just that and found that, when looking at the dollar value people place on privacy, there might not be as much as a paradox as we suspected, and business can even learn to leverage the market value of privacy to better understand what they should (and shouldn’t) collect from consumers.
The new study, conducted by assistant professor at the London School of Economic Huan Tang, analyzed how much personal information users in China were willing to disclose in exchange for consumer loans. Official credit scores do not exist in China, so consumers typically have to give over a significant amount of personal information in order for banks to assess their credit. By looking at the decisions of 320,000 users on a popular Chinese lending platform, Tang was able to compare user’s willingness to disclose certain pieces of sensitive information against the cost of borrowing.
The results? Tang found that users were willing to disclosure sensitive information in exchange for an average of $33 reduction in loan fees. While for many in the U.S., $33 may not seem all that significant, $33 actually represents 70% of the daily salary in China, showing users place a significantly high value on their privacy. What’s more, on the bank’s side this translates to 10% decrease in revenue when they require users to disclosure additional personal information.
There are a number of important implications of these study for businesses. For one, it suggests, as Tang says, “that maybe there is no ‘privacy paradox’ after all,” meaning consumers’ online behaviors do, in fact, seem to show a value on protecting people’s right to privacy. While today businesses often utilize the data they collect to make money, by collecting everything and anything they can get their hands on, businesses may be losing significant revenue in lost business. According to Tang, collecting more information than necessary turns out to be inefficient. Instead, business can leverage the monetary value users place on their data to be more discerning when deciding what information to collect. If a piece of data is highly valued by consumers and has little direct economic benefits for a company, it may not be worth collecting. Of course, limiting data is a key tenet of Privacy by Design principles, which organization should be applying to our their practices in order to improve their privacy posture vis-a-vis GDPR and other privacy regulations. Limiting data also improves the organization’s cybersecurity posture because it reduces its exposure.
While it may seem counter intuitive in today’s standard practice of collecting as much data as possible, this study shows that limiting the data that is collected can be, according to Tang, a “win-win” for businesses and consumers alike.
by Doug Kreitzberg | Oct 16, 2020 | Cybersecurity, Passwords, Uncategorized

We do need to make sure that we are using strong passwords, but guidance has changed on the need to continually change those passwords. The National Institute for Standards and Technology (NIST), which codifies best practice cybersecurity controls, has updated their guidelines around digital identity. Instead of forcing individuals to change their passwords frequently and/or require a special characters or passwords which are more gibberish, they recommend creating long passwords out of pass phrases, such as “NIST passphrases make passwords easy!”. Long pass phrases are difficult to crack and yet memorable enough for the user.
Still, remember not to use the same password twice (use of a log in manager can help you here). Also, enable multi-factor authentication for applications which may have sensitive information (where you have to both key in a password and enter a code from your smart phone, as an example).

by Doug Kreitzberg | Sep 18, 2020 | Cybersecurity, Risk Culture, supplychain
Recently, we wrote about a study showing a connection between an increase in death rates and cybersecurity policies implemented after a data breach in the healthcare industry. We talked about the importance of ensuring that cybersecurity and operational interests are aligned. However, that study raises another, equally important point: hospitals shouldn’t wait for a breach to occur before implementing appropriate cybersecurity controls. This is a lesson that every industry should learn and is one of the main principles behind cyber resiliency: instead of just trying to prevent the worst from happening, we need to create a risk culture that assumes the worse will happen, then take steps to minimize its impact on essential operations.
And when it comes to the importance of cybersecurity and resiliency for our healthcare industry, the stakes couldn’t be higher. Within a period of two months in 2017, the healthcare industry across the globe was brought to its knees by two unrelated ransomware attacks. Strangely, neither of these attacks intended to target healthcare organizations. Instead, each attack contained a self-replicating virus that accidentally spread beyond their intended targets. But no matter the intentions, these attacks caused hundreds of millions of dollars in damage and affected 40% of healthcare delivery in the U.K.
Fast forward today and the potential consequences of such an attack—intentional or otherwise—on our healthcare system are clearer than ever. In his opening remarks at the CISA National Cybersecurity Summit, Josh Corman, visiting researcher at CISA and founder of I am the Calvary, put the stakes of healthcare cybersecurity into perspective. “In areas affecting the brain, the hearth, the lungs, where time matters, where minutes or hours could be the difference between life and death, mortality rates are affected if you can’t give time-sensitive health care.”
Corman joined CISA this spring to help assure the security of Operation Warp Speed, the U.S.’s initiative to rapidly develop and distribute vaccines, therapeutics, and diagnostics for COVID-19. “Now we need healthcare delivery more than we ever have,” Corman said, “Now an attack during a peak surge in traffic would be absolutely devastating.” And such attacks aren’t just hypothetical. According to one report, U.S. officials have already notified a number of healthcare companies about targeted threats. In particular, the biotech company Moderna, now in stage 3 of COVID-19 vaccine trails, has been targeted by hackers.
These examples drive home the potentially life and death implications of cyber resiliency. We can and should try and prevent attacks from happening, but the reality is that’s not enough. In his talk, Corman lamented a culture within healthcare cybersecurity to wait for “proof of harm” before taking corrective actions. Instead of waiting for harm to occur, Corman argued, a clear, “unmitigated pathway to harm” should be enough to trigger corrective action. This is a lesson that extends far beyond the healthcare industry. All organizations need to create a risk culture that acknowledges and prepares for the harsh reality that, in some shape or form, cyber incidents are going to happen. To prepare for this, Corman outlined a number of key questions every organizations should consider:
- How do you avoid failure?
- How do you capture, study, and learn from failure?
- How do you have a prompt and agile response to failure?
- How do you contain and isolate failure?
Today, attempts to hack, steal, and disrupt systems are not hypotheticals. They are the new normal. Alongside efforts to prevent cyber attacks, organizations needs to be prepared to minimize the impact these attacks will have on essential business and operations.
by Doug Kreitzberg | Sep 16, 2020 | Cyber Insurance, Cybersecurity, ransomware
According to a new report by Coalition, one of the nation’s cyber insurance providers, ransomware attacks make up 41% of all cyber insurance claims in the first half of 2020. Unfortunately, that’s the good news. That number is actually down by 18% since 2019. The bad news? While the frequency of ransomware attacks are down, the severity of attacks has risen dramatically.
In particular, cyber criminals are starting to demand more and more money from their victims. According to Coalition, ransomware claims are in general 2.5x higher than other cyber insurance claims across all industries. And demands continue to increase in dramatic fashion. Coalition’s report states that the average ransom demand increased 100% since 2019 and has already risen an additional 47% between Q1 and Q2 of this year.
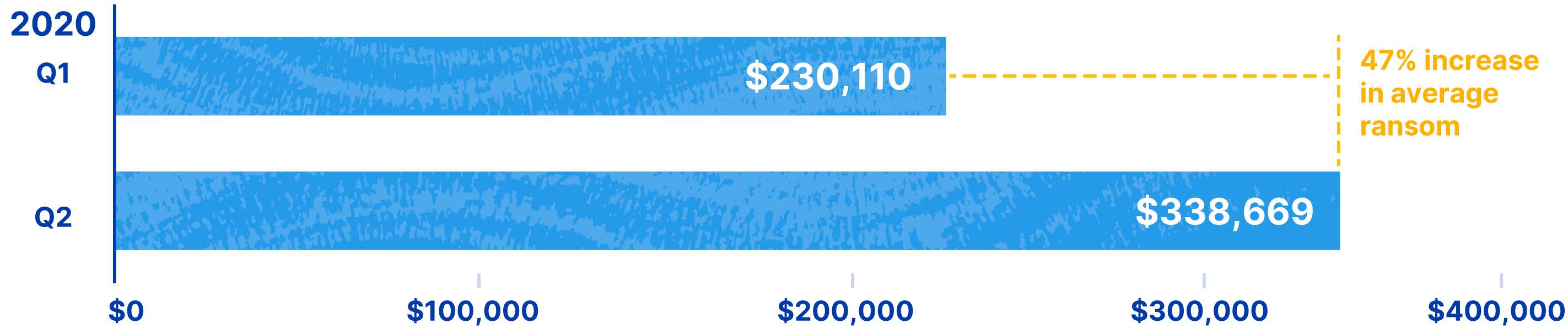
Source: Coalition
What’s more, not only have ransomware demands increased, but the attacks themselves are becoming more and more sophisticated. While traditional ransomware attackers encrypt data within the target’s network, now they are actually stealing the data and threatening to leak the information if a payment isn’t made, as happened to the cloud services firm Blackbaud this summer. This tactic may in part account for the of the increases in demands, as organization’s may be more motivated to pay in order to keep the incident private. However, there is no guarantee that paying will stop the attackers from leaking the data anyway.
While the Coalition report shows that more and more businesses are turning to cyber insurance to help with ransomware attacks, relying on insurance should not be your solution. Sure, insurance may help pay the cost of the ransom, but if attacks know insurance companies will pay up, they may start to feel confident asking for larger and larger amounts of money. The FBI also discourages businesses from paying demands.
Instead, the best response is prevention. Even simple solutions like multi-factor authentication and good password management can help dramatically. In addition, the report found that 60% of claims are for attacks that originated as a phishing or other social engineering scams. Investing in effective cyber awareness training can help prevent attacks from occurring in the first place. Like with most things related to cybersecurity, it’s always better to take action now rather than wait for the worst to happen.

by Doug Kreitzberg | Sep 14, 2020 | Business Continuity, Cybersecurity
Like everyone today, our elections officials have to grapple with technological changes. And with those changes comes emerging security concerns. Take the 2020 democratic Iowa caucus, for example. The Iowa Democratic Party decided to use a new app to record results of the caucus that ended up causing a myriad of problems, delaying the results and sparking a controversy about the party’s use of the app. As more states begin to digitalize the election process, election security has become a topic of national concern. Of course, the stakes of an incident is probably not as high for a business as, say, protecting the democratic process. However, when looking at a case with such high stakes, incidents in our elections can clarify what we expect not only from our government but also what consumers expect from companies, and what organizations need to be taking seriously. Here are just three areas from which business can learn from the issues surrounding election security.
Trust
The first thing that business and election security officials have in common is the need to maintain public trust. One of the biggest concerns with digitalizing our elections is, if something goes wrong with the technology, it may harm the public’s trust in the voting process. This was certainly the case in Iowa this year. Despite the party’s assurance that even with the app down the results of the caucus could be accurately counted, disinformation and confusion quickly spread online.
It’s not difficult to see how businesses can apply these election security concerns to their organizations. A public security issue with a produce or service could severely impact a business’s reputation and can be extremely difficult to repair. Consumers may feel like their privacy could be at risk and that your business doesn’t have their best interest in mind. To combat this, besides actively securing consumer data, businesses should be as transparent as possible with consumers about the organization’s cybersecurity efforts.
Management
Soon after the Iowa caucus, it become abundantly clear that the app developers and the Iowa Democratic Party made a number of mistakes that lead to the problems on caucus night. For example, before the night of the caucus, the app was only tested internally, with no external review. The IDP even declined an offer from Homeland Security to review the app before roll out. Developers also didn’t have time to get the app approved through app stores, so required users to download the app through testing software, effectively by-passing the need to meet the security requirements from app stores.
The list of ways that the rollout was mismanaged goes on and on. However, this only highlights the need for business management to be involved in ensuring proper cybersecurity best practices are followed through the entire product lifecycle, from initial development, to implementation, and on going maintenance.
Response Planning
Businesses should also look at how election security officials respond—or, perhaps more accurately, don’t respond— to issues that arise. Without a proper response plan in place, problems could worsen and cause enough confusion to allow disinformation about the issue to spread. And that’s exactly what happened in Iowa. As the problem with the Iowa caucus came to light, instead of deploying a carefully planned incident response, the whole night turned into chaos and confusion, as caucus leaders sat on hold for hours to deliver results or even text pictures of their tallies to party headquarters.
This example shows just how necessary it is for businesses to have a proper incident response plan in place. This should involve sitting down with business leaders, IT staff, and other relevant employees to write out a detailed response for every incident that could arise. With a plan in place, businesses should also conduct regular incident response simulations, by asking the response team to test their plan for each possible incident. Responding to an incident quickly and efficiently will not only help limit the impact of the issue, but could help show regulatory bodies your proactive stance to cyber incidents, and even save your business money.
With the general election looming, election security officials are working hard to ensure no problems arise on election day. Hopefully, come November there won’t be any lessons for businesses to learn from.

by Doug Kreitzberg | Sep 11, 2020 | Business Continuity, Cybersecurity, Risk Culture, Risk Management
Today business leaders are rightfully concerned about mitigating their organization’s cyber risks. To address this concern, many businesses have begun to hire individfuals responsible for cybersecurity and even hiring Chief Information Security Officers (CISOs) to provide security leadership at the executive level. But unfortunately, old habits die hard. Instead of integrating the cybersecurity team or the CISO into both cybersecurity and business conversations, many of these security leaders have become siloed from broader business strategy and goals. Of course, this also leaves the executive team under-informed about the nature and scope of their organization’s cyber risk profile.
One of the main tenants of a new security principle, cyber resiliency, stresses the need to integrate approaches to security and business in order for either side to succeed. In fact, organizations should even stop thinking of business and security as two opposing side of an equation and instead learn to see and promote the integration of each with the other. However, this will require both security experts and businesses leaders to put in some work.
Business-Aligned Security Leaders
A recent report by Forrester found that just four out of ten security leaders can answer the question, “How secure/at risk are we?” and less than half frequently consult business leaders before developing security strategies. This, to put it lightly, is a big problem. If security leaders are just focused on implementing and maintaining technical controls, they end up missing the bigger picture of the risk culture that surrounds those controls. It is vitally important for security teams to understand an organization’s business-critical assets and work with leadership to develop a risk mitigation plan that prioritizes those assets.
Cybersecurity teams also need to be able to communicate their needs to business leadership. According to the Forrester report, more than half of security leaders lack adequate skills in benchmarking their security programs. In order to integrate cybersecurity and business needs, security teams need to develop benchmarking and risk reports that they can properly communicate to business executives. Taking a more business-oriented approach to security can also help security leaders advocate for the funds they need to reduce risk.
Cyber-Aligned Business Leaders
Of course, in order for security leaders to effectively integrate business strategy into overall cybersecurity goals, the business executives and board members need to regularly meet and communicate with their security team. To ensure this happens, it’s important for board members to assume ultimate responsibility for oversight of the organization’s security and to integrate cybersecurity discussions into the overall business strategy, risk management, and budgeting. It may even be a good idea to require cybersecurity training for all board members to ensure everyone has a proper understanding of the current threat landscape and regulations.
With a focus on outcomes, training, and a security team able to communicate benchmarks and risk reports, board members will be in a position to properly define the organization’s cyber risk tolerance that is consistent with business strategy and current cybersecurity controls. Board members and executives teams must ensure the organization’s risk appetite is communicated throughout all levels of the organization and that they create a culture that reflects the cybersecurity and business interests of the organization. Many of these recommendations are included in a white paper from the World Economic Forum that details 10 essential principles and tools for boards to better integrate cyber resiliency with overall business strategy.
Today, most organizations understand the importance of maintaining an effective cybersecurity program. However, not many businesses are recognizing the interdependence of cybersecurity and business interests. And it’s a two way street. Both cybersecurity leaders and business executive and board members need to be mindful about taking a more holistic approach to cybersecurity and business for either to be effective.






