Ransomware Cyber Insurance Claim Amounts Skyrocket
According to a new report by Coalition, one of the nation’s cyber insurance providers, ransomware attacks make up 41% of all cyber insurance claims in the first half of 2020. Unfortunately, that’s the good news. That number is actually down by 18% since 2019. The bad news? While the frequency of ransomware attacks are down, the severity of attacks has risen dramatically.
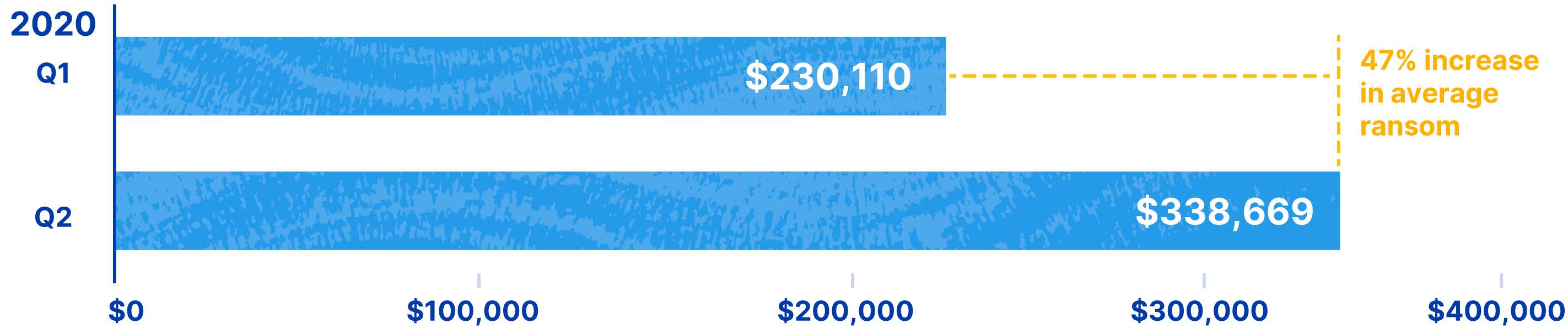
In particular, cyber criminals are starting to demand more and more money from their victims. According to Coalition, ransomware claims are in general 2.5x higher than other cyber insurance claims across all industries. And demands continue to increase in dramatic fashion. Coalition’s report states that the average ransom demand increased 100% since 2019 and has already risen an additional 47% between Q1 and Q2 of this year.
What’s more, not only have ransomware demands increased, but the attacks themselves are becoming more and more sophisticated. While traditional ransomware attackers encrypt data within the target’s network, now they are actually stealing the data and threatening to leak the information if a payment isn’t made, as happened to the cloud services firm Blackbaud this summer. This tactic may in part account for the of the increases in demands, as organization’s may be more motivated to pay in order to keep the incident private. However, there is no guarantee that paying will stop the attackers from leaking the data anyway.
While the Coalition report shows that more and more businesses are turning to cyber insurance to help with ransomware attacks, relying on insurance should not be your solution. Sure, insurance may help pay the cost of the ransom, but if attacks know insurance companies will pay up, they may start to feel confident asking for larger and larger amounts of money. The FBI also discourages businesses from paying demands.
Instead, the best response is prevention. Even simple solutions like multi-factor authentication and good password management can help dramatically. In addition, the report found that 60% of claims are for attacks that originated as a phishing or other social engineering scams. Investing in effective cyber awareness training can help prevent attacks from occurring in the first place. Like with most things related to cybersecurity, it’s always better to take action now rather than wait for the worst to happen.

Blackbaud Facing Lawsuit After Ransomware Attack
In July, we wrote about a ransomware attack suffered by the cloud computing provider Blackbaud that led to the potential exposure of personal information entrusted to Blackbaud by hundreds of non-profits, health care organizations, and educational institutions. At the time the ransomware attack was announced, security experts questioned Blackbaud’s response to the breach. Now, the Blackbaud ransomware attack isn’t just raising eyebrows, with the company facing a class action lawsuit for their handling of the attack.
Blackbaud was initially attacked on February 7th of this year. However, according to the company, they did not discover the issue until mid-May. While the time it took the company to detect the intrusion was long, it is increasingly common for threats to go undetected for long periods of time. What really gave security experts pause is how Blackbaud responded to the incident after detecting it.
The company was able to block the hacker’s access to their networks, but attempts to regain control continued until June 3rd. The problem, however, was that the hackers had already stolen data sets from Blackbaud and demanded a bitcoin payment before destroying the information. Blackbaud remained in communication with the the attackers until at least June 18th, when the company payed the ransom. Of course, many experts questioned Blackbaud’s decision to pay given that there is no way to guarantee the attackers kept their word. And, to make matters worse, the company did not public announce the incident to the hundreds of non-profits that use their service until July 16th — nearly two months after initially discovering the incident.
Each aspect of Blackbaud’s response to the ransomware attack is now a part of a class action lawsuit filed against the company by a U.S. resident on August 12th. The main argument of the lawsuit claims that Blackbaud did not have sufficient safeguards in place to protect the private information that the company “managed, maintained, and secured,” and that Blackbaud should cover the costs of credit and identity theft monitoring for those affected. The lawsuit also alleges that Blackbaud failed to provide “timely and adequate notice” of the incident. Finally, regarding Blackbaud’s payment of the ransomware demand, the lawsuit argues that the company “cannot reasonably rely on the word of data thieves or ‘certificate of destruction’ issued by those same thieves, that the copied subset of any Private Information was destroyed.”
Despite the agreement among privacy experts that Blackbaud’s response to the attack was anything but perfect, lawsuits pertaining to data breaches have historically had a low success rate in the U.S.. According to an attorney involved in the case, showing harm requires proving a financial loss rather than relying on the more abstract harm caused by a breach of privacy: “The fact that we don’t assign a dollar value to privacy [means] we don’t value privacy.”
Whatever the result of the lawsuit, questions still persist on whether Blackbaud’s response violates the E.U.’s General Data Protection Regulation. The GDPR requires organizations to submit notification of a breach within 72 of discovery. Because many of Blackbaud’s clients are UK-based and the company took months to notify those affected, it is possible Blackbaud could recevie hefty fines for their response to the attack. A spokesperson for the UK’s Information Commissioner’s Office told the BBC that the office is making enquiries into the incident.
As for the non-profits, healthcare organizations, and educational institutes that were affected by the breach? They have had to scramble to submit notifications to their donors and stakeholders that their data may have been compromised. Non-profits in particular rely on their reputations to keep donations coming in. While these organizations were not directly responsible for the breach, this incident highlights the need to carefully review third-party vendors’ security policy and to create a written security agreement with all vendors before using those services.

BEC and Ransomware: Following the Money
According to this year’s Cost of a Data Breach Report, the majority of malicious cyber attacks are financially motivated. So, when prioritizing risk, it makes sense to focus on cyber threats that have direct financial implications, such as ransomware and business email compromise (BEC) schemes.
Given the recent rise in ransomware attacks and the targeting of public agencies, it’s pretty likely you’ve seen some news about ransomware within the past year. And while it is certainly important to protect against the possibility of ransomware, that doesn’t mean less-publicized cyber attacks like BEC should be taken any less seriously.
In general, business email compromise involves scammers sending employees an email that looks as if it is coming from a familiar source requesting some sort of payment. Usually, scammers will impersonate frequently used vendors or even CEOs. And these scams can be costly. Last year Nikkei, a Japanese media company, suffered a loss of $29 million when a scammer impersonated a company executive.
In fact, BEC scams have repeated topped the FBI’s annual Internet Crime Report as the costliest form of cyber crime. And, when you compare the costs of BEC and ransomware attacks, it becomes pretty clear which one poses the greater risk.
[table id=1 /]
While FBI’s report shows a sharp increase in ransomware losses in recent years, BEC scams continue to outpace ransomware by a staggering margin. If you were responsible for prioritizing risk activities in your organization, where would you focus? When you follow the money, the answer is pretty obvious. The good news, however, is that a lot of the procedures, guidelines, and training that can be done to prevent BEC can also help ransomware, such as anti-malware software and email authentication. It can be easy to base your cybersecurity processes off of what you see in the headlines, but that won’t always give you an accurate view of your risk profile. It’s essential to conduct regular risk assessments to gain a clear understanding of the biggest threats your organization faces.

Blackbaud Breach Leaves Hundreds of Non-Profits Scrambling
This month Blackbaud, a cloud computing provider primarily serving nonprofits and educational institutions, announced that the company suffered a ransomware attack back in May. The company’s response, however, has raised more than a few eyebrows from security experts, and left hundreds of nonprofits scrambling to figure out if they’ve been affected. The Blackbaud breach is just the latest reminder that third party data processors can be a liability to your business.
According to Blackbaud’s statement about the breach, the company quickly discovered the attack and was able to remove the attackers from their systems — but not before the hackers stole a copy of a data set. Blackbaud has not specified the exact nature of that data, but claims it does not include sensitive information such as credit card information, bank account information, or social security numbers. On source told the BBC, however, that the stolen data involves donor information from hundreds of nonprofits and institutions and includes details such as names, addresses, ages, and estimated wealth. Now, organizations that are customers of Blackbaud are scrambling to see if their donors’ information was included in the breach and, if so, must release data breach disclosures of their own.
The most egregious part of the Blackbaud breach, however, was the company’s response. When they discovered their data had been stolen, they agreed to pay a ransom to have the attackers delete that data. Subsequently, Blackbaud assured their customers that there is no reason to believe the stolen data “was or will be misused; or will be disseminated or otherwise made available publicly.” However, cybersecurity experts have been quick to point out that this is a dangerous assumption to make.
Firstly, they got ransom’d but sounds like the actor also had a copy of the data. They paid the ransom and somehow believe that the (criminal) actor kindly removed their copy of the @blackbaud data: https://t.co/VrR5my2S8U
— Troy Hunt (@troyhunt) July 30, 2020
Despite Blackbaud’s insistence that the data has been deleted by the hackers, the company has not stated why they are confident in that assumption, and no external investigation has been able to confirm it. As many have noted, Blackbaud’s response to the breach seems more an attempt to protect their brand’s reputation, rather than a transparent disclosure. There are also questions about the amount of time the company took to disclose the breach, and whether or not that violates GDPR requirements.
The fact that so many questions about the Blackblaud breach are still unanswered two weeks after it was announced has not been assuring to the nonprofits that use their services. Over 100 organizations have already notified their donor’s about the breach, and more will likely do so in the weeks ahead.
While this far from the only third-party provider to suffer a data breach, the attack on Blackbaud is a rather stark example of why businesses need to take the time to carefully evaluate third-party security practices, as well as insist on strong agreements that define accountability and responsibilities in the event of an incident. This is especially important for associations and non-profits because their very existence relies on the trust that their members or donors place in them. When that trust is violated, it takes a long time to repair.

Ransomware Attackers are Playing the Long Game
Over the past few years, ransomware has become a more and more common form of cyber attack. In part, this is because hackers have started to sell pre-made packages that anyone can buy on the dark web and run without a lot of technical know-how. While this form of ransomware allows malicious code to spread automatically, it’s not always the most sophisticated form of attack. This may be why human-operated ransomware has become more popular over the past few months. Unlike pre-coded ransomware that blindly crawls through infected networks, human-operated ransomware attacks tend to play more of the long game. Once attackers gain access to a victim’s system, they take their time to gather as much intel as possible about their target, often waiting months before launching their attack. This helps them gain access to other areas within the network and ultimately make it extremely difficult for the victim to put a stop to the attack once it starts.
The key to combatting these more sophisticated attacks, then, is to stop them from accessing your systems in the first place. Often, ransomware attacks gain access by taking the path of least resistance, such as unpatched applications. This has been an especially big problem for the healthcare industry recently. As hospitals continue to be overwhelmed by COVID-19, they have not had the time and resources to safeguard security systems and update applications quickly.
For example, recently human-operated ransomware attackers are using out of date virtual private networks (VPNs) to gain access. In fact, Microsoft identified “several dozens of hospitals” that were vulnerable to attack because of outdated VPN applications. To help combat this issue, Microsoft has developed a new alert system to notify hospitals that have unpatched applications and other vulnerabilities.
With ransomware attackers playing the long game, it’s vitally important to ensure your systems and applications are patched and that you fix any known vulnerabilities. In addition, any potential compromise to your system, however small, should be investigated and dealt with as soon as possible. Otherwise, hackers can spend months moving throughout your networks undetected and make it near impossible to remove once they launch their attack.