
by Kathleen L | Feb 10, 2022 | Cybersecurity, Social Media
Social media platforms like LinkedIn, Twitter, and Facebook, as well as simple text messages have become a popular vector for phishing attacks. As phishers step up their scams, organizations need to keep their employees informed on how to spot them.
LinkedIn
LinkedIn is widely considered a trusted domain. This means that any malicious emails that are leveraging LinkedIn most likely will not get blocked by your anti-spam and malware filters. The “redirect” feature for business on LinkedIn that allows you to track ad campaign performance can also unfortunately be used by hackers to redirect users to phishing scams. If you are unsure whether a message is legitimate or not, take a pause and do your own research on the site or service in question.
Twitter
You may have heard of the July 15th Twitter hack that compromised high-profile, verified Twitter accounts. This phishing attack sent out fake tweets with links to a phishing site designed to steal cryptocurrency. Although people were scammed out of money, it could have been much worse, and information could have easily been stolen. If this type of scam can happen to celebrities, political leaders, and large corporations, it can happen to anyone.
Facebook
Earlier this year, Facebook users were warned of phishing campaigns disguised as Messenger chats. When it comes to Facebook, if you are getting unprompted messages from friends or people you know, asking you to click a link or provide any information, just ignore it. If you think it may be legitimate or important, reach out to that person with another means of communication and ask them to be sure.
SMS
As if social media scams aren’t bad enough, mobile phishing scams are becoming more popular than ever. With all the buttons and ads that pop up on your phone, it can be easy to let your guard down when it comes to mobile phishing scams. Then there is SMS phishing, which can install malware on your device and significantly control your device functionality. If you receive a suspicious text message, do not open it, and absolutely do not click on any links.
All it takes is one click for a hacker to compromise your device. Mobile security should be a top priority for any organization. With more employees using mobile devices for work and having their social media apps such as LinkedIn on their phones, organizations need to step up their anti-phishing capabilities to keep users secure no matter what device they are working from. Organizations should be including regular security awareness training to help employees understand these threats and how they target individuals and businesses. Phishing can come from any source, and you need to be suspicious of any and every suspicious message or link you come across.
by Kathleen L | Jan 20, 2022 | Compliance, Cybersecurity
The Federal Trade Commission (FTC) released an alert, warning companies that they may face legal penalties if they aren’t taking the proper steps to mitigate Log4j vulnerabilities to protect consumer information. Earlier this month, FTC officials said there is a “severe risk” to consumer products, software, and applications caused by a vulnerability in the Java logging package. This vulnerability is being exploited by hackers and it is critical that vendors who rely on Log4j take the proper precautions to reduce their likelihood of an attack.
An example of this is the Equifax breach, which was caused by failing to patch a known vulnerability. Because of this vulnerability, the personal information of 147 million consumers was left exposed. Equifax paid $700 million to settle actions taken by the FTC. The FTC intends to pursue any companies that fail to take steps to protect consumer data from exposures caused by Log4j, or similar vulnerabilities that may occur in the future.
The FTC advises companies to keep your Log4j software package updated to the most recent version, and reference Log4j Vulnerability Guidance provided by CISA. This FTC alert is a wake-up call to many companies that cyber threats are evolving, and so are security requirements and legal actions that will be taken if they do not take the proper steps to protect consumer information.

by Doug Kreitzberg | Dec 14, 2021 | Cybersecurity, Uncategorized
With increasing requests from clients regarding their cybersecurity controls, companies are looking to us to help in a number of areas, with questions about written security policies, vulnerability and penetration testing, risk assessments, and security awareness training. These questions and concerns, which were mainly targeted towards large companies are now also crucial for small and medium-sized businesses.
In addition to the previously mentioned topics, clients are looking to see that companies have certain security tools in place such as:
- Multi-Factor Authentication (MFA): MFA is a keyway to provide an extra layer of security to prevent hackers from accessing your system. MFA is when an alternate means of identification, in addition to a password is necessary to log in.
- Endpoint Detection and Response (EDR): EDR is a cyber security solution that continuously monitors, collects data, and responds to help mitigate cyber threats.
- Backup: Companies should be sure to include multiple forms of backup with at least one stored off-site. Backups should also be regularly tested to ensure they can be restored as needed.
- Patching: Patches are software and operating updates that help address any vulnerabilities and keep your system up to date.
If your company is getting overwhelmed by client requests about your security posture, you are not alone. If you think your current measures may not be up to par or do not have the time, Designed Privacy created a program that provides you with a guide to cybersecurity and the tools you need to keep your company and your clients protected and stay competitive.

by Doug Kreitzberg | Dec 10, 2021 | Cyber Awareness, Cybersecurity, Data Breach, Human Factor
This Fall, the personal health information of over 170,000 dental patients was exposed in a data breach associated with the Professional Dental Alliance, a network of dental practices affiliated with the North American Dental Group. According to the Professional Dental Alliance, patient information was exposed due to a successful phishing attack against one of their vendors, North American Dental Management. The phishing campaign gave attackers access to some of NADM’s emails, where the personal information of patients were apparently stored.
While the Professional Dental Alliance has said their electronic dental record system and dental images were not accessed, an investigation found that the protected health information of patients such as names, addresses, email addresses, phone numbers, insurance information, Social Security numbers, dental information, and/or financial information were accessed by the attackers.
This is not the first time dental offices have found themselves the target of a data breach. In 2019, a ransomware attack against a managed service provider resulted in the exposure of patient information from over 100 Colorado dental offices. A year later, the information of over 1 million patients was exposed after an attack against the Dental Care Alliance.
These incidents reveal just how vulnerable professionals can be against cybersecurity attacks and data breaches. One of the reasons for this is because many professionals are small businesses who don’t have the time or expertise to deal with everything that goes into cybersecurity. So, many professionals rely on vendors and associations to ensure they are protected. The issue is, if those vendors and associations experience a breach, professionals are also at risk.
To keep their patient information safe, it’s vital that dental offices and all professional businesses pay attention to some of the human risks that can lead to cybersecurity incidents. The attack this week, for instance, was the result of a phishing attack that tricked an employee into handing over account credentials. Here are a few things all professionals can easily do on their own to stay secure:
Endpoint detection and prevention
Endpoint detection and response (EDR) is a type of security software that actively monitors endpoints like phones, laptops, and other devices to identify any activity that could be malicious or threatening. Once a potential threat is identified, EDR will automatically respond by getting rid of or containing the threat and notifying your security or IT team. EDR is vital today to stay on top of potential threats and put a stop to them before they can cause any damage.
Multi-Factor Authentication
Using multi-factor authentication (MFA) is a simple yet powerful tool for stopping the bad guys from using stolen credentials. For example, if an employee is successfully phished and the attack gets that employee’s login information, having MFA in place for that employee’s account can stop the attacker from accessing their account even if they have the right username and password. If possible all users accessing your system should have multi-factor authentication set up for all of their accounts. At minimum, however, it is extremely important that every user with administrative privileges use MFA, whether they are accessing your network remotely or on-premise.
Patching
Hackers are constantly looking for vulnerabilities in the software we rely on to run our businesses. All those software updates may be annoying to deal with, but they often contain important security features that “patch up” known vulnerabilities. At the end of the day, if you’re using out-of-date software, you’re at an increased risk for attack. It’s therefore important that your team stays on top of all software updates as soon as they become available.
Back-ups
Having a backup of your systems could allow you to quickly restore your systems and data in the event of an attack. This is especially important if you are hit by ransomware, in which the attackers remove your data from your networks. However, it’s essential to have an effective backup strategy to ensure the attackers don’t steal your backups along with everything else. At minimum, at least one backup should be stored offsite. You should also utilize different credentials for each copy of your backup. Finally, you should regularly test your back-ups to ensure you will be able to quickly and effectively get your systems online if an attack happens.
Security Awareness Training
As this latest data breach shows, phishing and social engineering attacks are common ways attackers gain access to your systems. Unfortunately, phishing attacks are not something you can fix with a piece of software. Instead, its essential employees are provided with the training they need to spot and report any phish they come across. Sometimes it only takes one wrong click for the bad guys to worm their way in.

by Doug Kreitzberg | Aug 11, 2021 | Compliance, Cybersecurity
While cyber attacks such as ransomware have steadily increased in frequency over the past few years, more recent, widely publicized attacks like the Colonial Pipeline attack have finally caused government agencies to sit up and start taking action. The White House’s unprecedented executive order, for example, aims to help modernize the federal government’s cybersecurity practices, and the FBI recently requested an additional $40 million for cybersecurity defenses. While these important steps are aimed at strengthening the government’s response to cyber threats, other government agencies are now starting to issue updated guidelines for regulated industries. Much of these new guidelines cover a lot of the basics of cybersecurity practices, like creating a cybersecurity policy and encrypting sensitive data. However, what becomes clear is that for regulated industries to fully adopt these guidelines there must be a focus on managing and mitigate the human risks involved in cybersecurity.
Of the various government agencies issuing new cybersecurity guidelines, the U.S. Department of Labor’s Employee Benefits Security Administration guidelines is notable for being the first time the department has issued any sort of cybersecurity guidance. The guidelines are aimed at entities covered under the Employee Retirement Income Security Act, including “benefit plan sponsors, plan fiduciaries, record keepers and plan participants” and are designed to protect the estimated $9.3 trillion in assets the department oversees. Included in the guidelines are practices widely considered essential for defending against cyber threats, including a formal cybersecurity policy, annual risk assessments, and conducting security reviews of 3rd party vendors.
Many of the guidelines issued by the Department of Labor are aligned with the New York Department of Financial Service’s 2017 cybersecurity regulation, which itself is starting to ramp up its own guidelines. In June, the NYDFS released updated FAQ’s that offer further guidance on complying with the state regulation while also releasing new ransomware guidelines. The updated FAQ shows the department is not messing around. While the NYDFS outline which covered entities can file for an exemption, they also emphasize that even exempt entities must comply with certain aspects of the regulation, such as maintaining a cybersecurity policy, conducting risk assessments, and notifying the department of any cybersecurity events. In their ransomware guidance, the department cites the importance of practices such as cyber awareness training, MFA and password management, and strong access privilege restrictions — all of which are already required under the department’s regulation.
While many of the cybersecurity guidelines government agencies are now offering cover some of the basic cybersecurity practices, implementing and maintaining these guidelines can be pretty daunting for a business to try to put in place. What becomes clear is that even the technical aspects of cybersecurity involve managing and mitigating human risks. For example, the NYDFS urges covered entities to implement a patch management program, which requires leadership ensuring their IT team regularly apply patches to the organization’s software and systems. If their IT fails to do this, they could be slapped with millions in fines. It’s therefore essential businesses focus not only on staying compliant, but also ensuring their teams are developing habits that align with their cybersecurity needs. Managing these human risks first and foremost involve three factors: keeping tasks simple, using prompts for employees, and providing positive feedback. In combination, these three factors will help to ensure employees can develop and sustain these habits that, ultimately, can make or break an organization’s cybersecurity posture.

by Doug Kreitzberg | Dec 28, 2020 | Business Continuity, Cybersecurity
Earlier this year we wrote about the fact that cyber attacks cost businesses millions of dollars per incident. But what about the cost of cybercrime on larger scale? This month, McAfee released a new report analyzing at the cost of cybercrime globally, and the findings are staggering.
The most startling news from the report is the jump in the overall cost of cybercrime globally. Between 2018 and 2020, McAfee found a nearly 50% increase in average global cost. Now, the estimated global cost of cybercrime is $945 billion — more than 1% of the global GDP.
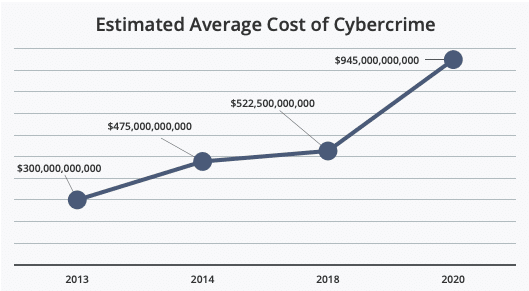
Source: McAfee
Just as startling, however, is that the report found a myriad of additional damages organizations face after a cyber incident beyond direct financial costs. In their report, McAfee found that 92% of organizations surveyed identified “hidden costs” that effected them beyond direct monetary losses. These hidden costs can have long terms effects on an organization’s productivity and ability to prevent future attacks.
One of the main hidden costs the report covers is the “damage to company performance” after a cyber incident. These damages, according to the report, is primarily related to a loss in productivity and lost work hours as businesses attempt to recover from an attack — usually because system downtime and disruptions to normal operations. While these losses might be, to some extent, inevitable following an attack, McAfee’s report found that organizations routinely neglect one essential aspect of cybersecurity: communication within the organizations.
We’ve talked before about the importance of creating an incident response plan, but without communication and cooperation between all areas of an organization, these plans won’t be all that effective. According to the report, IT decision makers think some departments aren’t ever made aware that a cyber incident even happened. The breakdown in communication is especially damaging between IT and business leadership. “IT and line-of-business (LOB) decision makers,” the report says, “have different understandings of what, why, and how a company or government agency is experiencing an IT security incident.” In fact, the lack of communication goes so far as whether or not there is even a response plan at all. The report found that, in general, business leadership often believe there is a response plan in place when there isn’t one.
This lack of communication also extends to the nature and scope of an organization’s cyber risk. The report noted a significant lack of organization-wide understand of cyber risk, which, the report states, “makes companies and agencies vulnerable to social engineering tactics. Once a user is hacked, they do not always recognize the problem in time to stop the spread of malware.”
While there will almost always be disruptions and hidden costs following a cyber incident, McAfee’s report seems to indicate many of these losses are self-inflicted. The report shows that the most common change organizations make after a cyber incident is investment in new security software. And, while technical safeguards are certainly necessary, they are far from sufficient. Instead, organizations need to begin investing in policies and procedures that ensure organization-wide communication, knowledge, and response to cyber risk and incidents.





