
by Doug Kreitzberg | Aug 31, 2020 | Cyber Awareness
When it comes to cybersecurity training, it’s easy to focus your energy on employees who may not have an advanced understanding of your network and technological systems. And, of course, it is vitally important these employees understand the basics of cybersecurity and adopt behaviors that help protect your systems from compromise. However, implicit in this way of thinking is that your IT staff, who are incredibly knowledgable about your systems, don’t need to be trained in cybersecurity. This couldn’t be further from the truth.
While your IT team is likely more aware of existing cyber threats, they also likely have administrative access across your entire network, making their account far more costly if compromised. What’s more, IBM’s 2020 Cost of a Data Breach Report found that 19% of all malicious attacks are initially caused by cloud misconfigurations, which is generally the responsibility of IT staff.
It is therefore vitally important to ensure your IT team is receiving role-specific cybersecurity training alongside the rest of your staff. This training should still cover a lot of the basics that every employee needs to know, but it should also include more specific and in-depth training in topics such as cloud configurations, access management and monitoring, network segmentation, and vulnerability scans. Your entire IT staff doesn’t need to be security experts, but everyone should have a good understanding of the current threat landscape and know how to spot any suspicious activity within your systems.
And, like all cybersecurity training, it’s important to use a program that focuses on helping your team build better, more secure habits, rather than simply throwing information at them. An important aspect of this is to simply make it easier for your IT team to do the job they need to do and do it securely. Because IT departments have highly specialized knowledge, it can be easy for business leadership to simply leave them to do what they think makes sense. However, executives should be actively involved in giving immediate feedback and listening to what IT staff need to make sure they can do their jobs efficiently and safely.
by Doug Kreitzberg | Aug 28, 2020 | Business Email Compromise, Cybersecurity, social engineering
Last week we wrote about the significant cost of business email compromise (BEC) scams compared to other, more-publicized cyber attacks. Now, the cybersecurity firm Agari has published a report showing a new BEC threat emerging — one that is more sophisticated and more costly than what we have seen in the past.
Business email compromise threats are a form of social engineering scams that have been around for a long time. “Nigerian prince scams,” for example, are what people often think of when they think of these types of attacks. However, as technology and modes of communication have gotten more sophisticated, so too have the scammers. Agari’s new report details the firm’s research on a new gang of BEC scammers based in Russia that call themselves “Cosmic Lynx.”
Unlike most BEC scams that tend to target smaller, more vulnerable organizations, the group behind Cosmic Lynx tends to go after gigantic corporations — most of which are Fortune 500 or Global 2000 companies. While larger organizations are more likely to have more sophisticated cybersecurity protocols in place, that doesn’t mean they can’t be tricked, and the payout for successful scams is significantly larger. The average amount requested through BEC is typically $55,000. Cosmic Lynx, on the other hand, requests $1.27 million on average.
How Does it Work?
While the basic’s of Cosmic Lynx’s BEC attacks are pretty standard, the group uses more advanced technology and social engineering tactics to make their scams more successful.
Typically, Cosmic Lynx uses a “dual impersonation scheme” that mimics indidvuals both within and outside of the target of the scams. Moreover, by manipulating standard email authentication settings and registering domains that imitate common secure email domains (such as secure-mail-gateway[.]cc), the group is able to convincingly spoof their email address and display name to look almost identical to a employees within the targeted business. Acting as the CEO, the group will typically send an email to a Vice President or Managing Director notifying them of a new acquisition and referring the employee to an external legal team to finalize the deal and transfer funds.
Cosmic Lynx will then impersonate the identity of a real lawyer and send the employee an email explaining they are helping to facilitate the payment. Of course, organization receiving the funds is actually a mule account — typically Hong Kong-based — controlled by Cosmic Lynx.
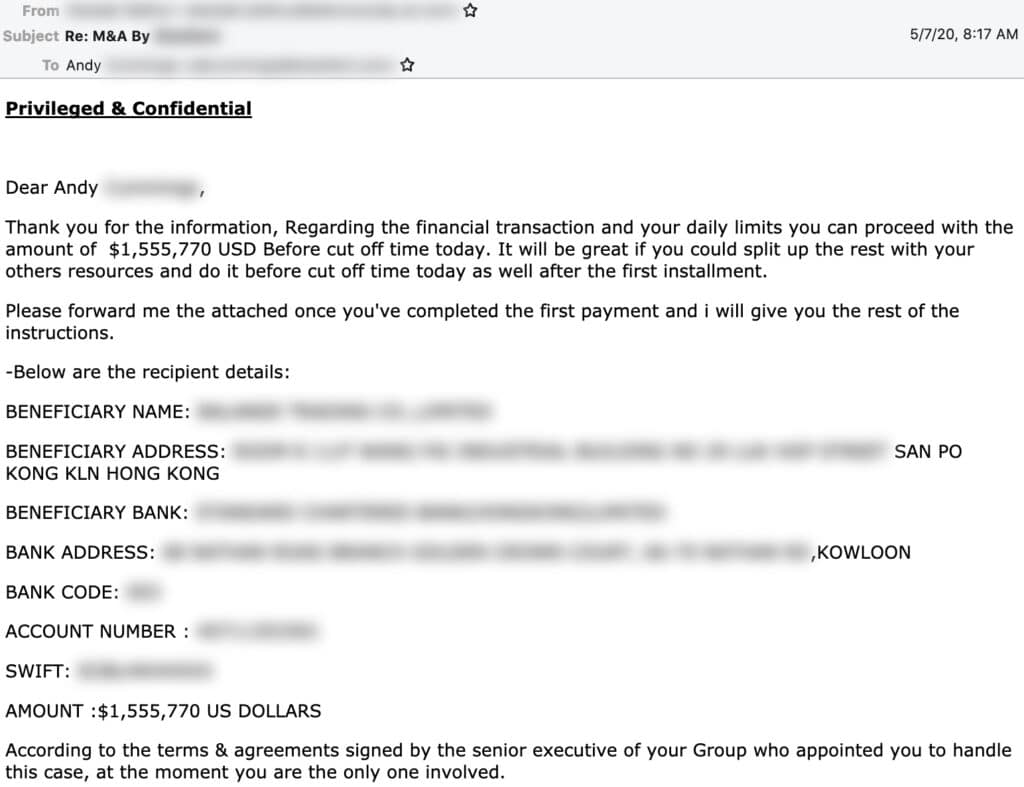
Source: Agari
For now, Cosmic Lynx seems to be the only group carrying this new BEC threat, however it is very likely other groups, seeing the amount Cosmic Lynx is raking in, will begin to follow suit. Simply put, the level of sophistication involved in these scams will require businesses to have more sophisticated protections in place to prevent this new threat. While more advanced email filters may help to detect spoofed email addresses, the most effective method to prevent BEC scams is to have strong policies in place to verify payment requests before releasing funds.
by Doug Kreitzberg | Aug 26, 2020 | Cybersecurity, Identity
When we think about cybersecurity, we usually think about it in terms of an inside and an outside. You have your network, application, and data all instead one system, and cybersecurity is about keeping the bad guys on the outside. For awhile, this “castle and moat” model of cybersecurity made a lot of sense. However, as technology has advanced and business needs have changed, experts are now shifting towards a new way of thinking about cybersecurity: zero trust.
The problem with the traditional approach to cybersecurity is that the lines between inside and outside are now blurred. Instead of keeping all our applications and data in a central location, the introduction of cloud-based services has spread out our network into multiple locations with multiple points of access. What’s more, with the recent rise in remote work, our networks are less centralized than ever before.
In many ways, hackers have understood the implications of these changes far faster than we have. Today, brute force attacks have taken a backseat to credential compromise, phishing, and other attacks that allow bad actors to gain access by using your network settings rather than breaking them. And if you use the traditional cybersecurity model, once a hacker gains access to your network, they can spend months freely moving around your network before launching an attack.
That’s why cybersecurity experts are pushing what is called “zero trust” cybersecurity. In essence, this strategy involves verifying the identity and access needs of every single user — no matter if they are coming from inside or outside your network. Instead of assuming that it’s okay to trust anyone already in your network, zero trust means everyone should be mistrusted until proven to be legitimate.
One aspect of zero trust involves using technology to secure your network from the inside out. Multi-factor authentication, network segmentation, and identity and access management systems are all key tools for a zero trust security posture. It’s important to keep a close watch on the access employees have to move around your network. Best zero trust practice means only giving access to an employee for specific business needs then revoking that access after a fixed period of time. Using these practices can help protect your network if an employee’s credentials are compromised.
While using cybersecurity technology will help you build towards a zero trust framework, without proper governance structures and an overall zero trust culture your organization will remain vulnerable. It’s essential that business leadership understands the concept of zero trust and are active in crafting a culture that values this model of security. If an employee receives an invoice from a vendor, for example, it should be standard procedure to verify the identity of the vendor and the payment request before releasing funds.
At the end of the day, a zero trust approach to cybersecurity requires an active and ongoing effort to prevent cyber threats. Security technology, policies, and culture should be built into your business strategy by design rather than retroactively applied.

by Doug Kreitzberg | Aug 24, 2020 | Business Email Compromise, ransomware, Risk Management
According to this year’s Cost of a Data Breach Report, the majority of malicious cyber attacks are financially motivated. So, when prioritizing risk, it makes sense to focus on cyber threats that have direct financial implications, such as ransomware and business email compromise (BEC) schemes.
Given the recent rise in ransomware attacks and the targeting of public agencies, it’s pretty likely you’ve seen some news about ransomware within the past year. And while it is certainly important to protect against the possibility of ransomware, that doesn’t mean less-publicized cyber attacks like BEC should be taken any less seriously.
In general, business email compromise involves scammers sending employees an email that looks as if it is coming from a familiar source requesting some sort of payment. Usually, scammers will impersonate frequently used vendors or even CEOs. And these scams can be costly. Last year Nikkei, a Japanese media company, suffered a loss of $29 million when a scammer impersonated a company executive.
In fact, BEC scams have repeated topped the FBI’s annual Internet Crime Report as the costliest form of cyber crime. And, when you compare the costs of BEC and ransomware attacks, it becomes pretty clear which one poses the greater risk.
[table id=1 /]
While FBI’s report shows a sharp increase in ransomware losses in recent years, BEC scams continue to outpace ransomware by a staggering margin. If you were responsible for prioritizing risk activities in your organization, where would you focus? When you follow the money, the answer is pretty obvious. The good news, however, is that a lot of the procedures, guidelines, and training that can be done to prevent BEC can also help ransomware, such as anti-malware software and email authentication. It can be easy to base your cybersecurity processes off of what you see in the headlines, but that won’t always give you an accurate view of your risk profile. It’s essential to conduct regular risk assessments to gain a clear understanding of the biggest threats your organization faces.

by Doug Kreitzberg | Aug 21, 2020 | Risk Culture
When we think of risk — especially in cybersecurity — we usually think about the things we do that can hurt us: clicking on that phish, accidentally forwarding an email to the wrong party, wiring money to the wrong (or fraudulent) bank account.
However, we should also pay attention to what we don’t do, such as failing to patch the system as soon as an update is available, failing to act on findings in a vulnerability scan, failing to change or strengthen our passwords, failing to add multi-factor authentication, or failing to review logs. Sometimes, our ability to accept “passive risk,” such as putting off taking an action to another day can be more pernicious than active risk. In fact, misconfigurations — a form of passive risk — is a top threat factor, according to Verizon’s 2020 Data Breach Investigations Report.
A recent paper describes a series of studies conducted that assess employees’ level of passive risk. According to the results, those that stated that their tolerance for passive risk was high also exhibited those passive risk cybersecurity behaviors. Interestingly, however, the study did not find the same correlation between active risk assessments and active risk behaviors.
So, how can you address passive risk? Design the behaviors that you would like to see and test changes in processes with the staff that seems most prevalent to passive risk. One example is to facilitate the automation of patching so that it makes it easy for the IT staff to perform. Another option is to take the time to fine tune log alerts so that the team does not have to deal with a lot of false positives. The paper also suggests changing the wording of certain security features to highlight the consequence of passive risk behavior. For example, instead of referring to passwords as “strong” or “weak,” using phrases such as “low risk” or “high risk” passwords can help drive home the potential consequence of poor credential management.
Whatever methods you use, In today’s remote environment, it’s always important to take the time to get together with your team and bond with them. Having a better relationship with your team can help generate the cohesion that is necessary for a risk-aware culture.





