
by Doug Kreitzberg | Dec 9, 2020 | Business Email Compromise, Data Breach, Disinformation, Human Factor, Phishing
Yesterday, I received an email from a business acquaintance that included an invoice. I knew this person and his business but did not recall him every doing anything for me that would necessitate a payment. I called him to about the email and he said that his account had been indeed hacked and those emails were not from him. What occurred was an example of business email compromise (BEC) using stolen credentials.
Typically, BEC is a form of cyber attack where attackers create fake emails that impersonate executives in order to convince employees to send money to a bank account controlled by the bad guys. According to the FBI, BEC is the costliest form of cyber attack, scamming business out of $1.7 billion in 2019 alone. One reason these attacks are becoming so successful is because attackers are upping their game: instead of creating fake email address that look like a CEO or a vendor, attackers are now learning to steal login info to make their scams that much more convincing.
By compromising credentials, BEC attackers have opened up multiple new avenues to carry out their attack and increase the change of success. Among all the ways compromised credentials can be used for BEC attacks, here are 3 that every business should know about.
Vendor Email Compromise
One way BEC attackers can use compromised credentials has been called vendor email compromise. The name, however, is a little misleading, because vendors aren’t actually the target of the attack. Instead, they are the means to carry an attack out on a business. Essentially, BEC attackers will compromise the email credentials of an employee at the billing department of a vendor, then send invoices from that email to businesses requesting they make payment to a bank account controlled by the attackers.
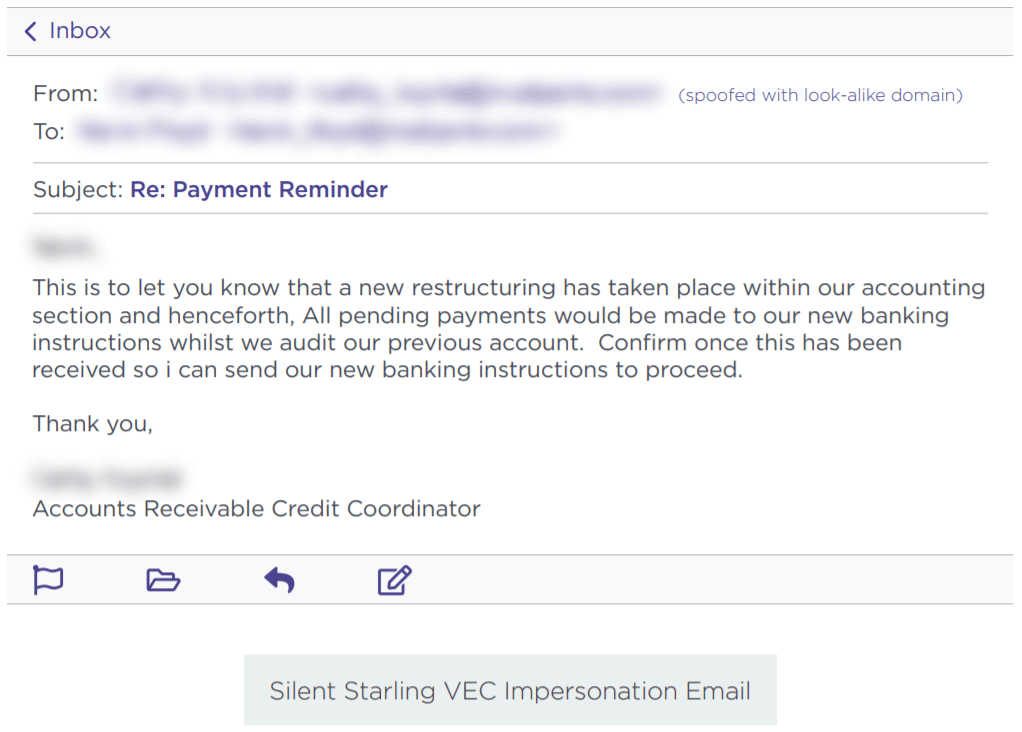
Source: Agari
Inside Jobs
Another way attackers can use compromised credentials to carry out BEC scams is to use the credentials of someone in the finance or accounting department of an organizations to make payment requests to other employees and suppliers. By using the actual email of someone within the company, payments requests look far more legitimate and increase the change that the scam will succeed.
What’s more, attackers can use compromised credentials of someone in the billing department to even target customers for payment. Of course, if the customers make a payment, it goes to the attackers and not to the company they think they are paying. This is a new method of BEC, but one that is gaining steam. In a press release earlier this year, the FBI warned of the use of compromised credentials in BEC to target customers.
Advanced Intel Gathering
Another method to use compromised credentials for BEC doesn’t even involve using the compromised account to request payments. Instead, attackers will gain access to the email account of an employee in the finance department and simply gather information. With enough time, attackers can study who the business releases funds to, how often, and what the payment requests look like. With all of this information under their belt, attackers will then create a near-perfect impersonation of the entity requesting payment and send the request exactly when the business is expecting it.
Attackers have even figured out a way to retain access to employee’s emails after they’ve been locked out of the account. Once they’ve gained access to an employee’s inbox, attackers will often set the account to auto-forward any emails the employee receives to an account controlled by the attacker. That way, if the employee changes their password, the attacker can still view every message the employee receives.
What you can do
All three of these emerging attack methods attack should make businesses realize that BEC is a real and dangerous threat. It can be far harder to detect a BEC attack when the attackers are sending emails from a real address or using insider information from compromised credentials to expertly impersonate a vendor. Attackers can gain access to these credentials in a number of ways. First, through initial phishing attacks designed to capture employee credentials. Earlier this year, for example, attackers launched a spear phishing campaign to gather the credentials of finance executives‘ Microsoft 365 accounts in order to then carry out a BEC attack. Attackers can also pay for credentials on the dark web that were stolen in past data breaches. Even though these breaches often involve credentials of employees’ personal accounts, if an employee uses the same login info for every account, then attackers will have easy access to carry out their next BEC scam.
While the use of compromised credentials can make BEC harder to detect, there are a number of things organizations can do to protect themselves. First, businesses should ensure all employees—and vendors!—are properly trained in spotting and identifying phishing attacks. Second, organizations should require proper password management is for all users. Employees should use different credentials for every account, and multi-factor authentication should be enabled for vulnerable accounts such as email. Lastly, organization should disable or limit the auto-forwarding to prevent attackers from continuing to capture emails received by a targeted employee.
Businesses should also ensure employees in the finance department receive additional BEC training. A report earlier this year found an 87% increase in BEC attacks targeting employees in finance departments. Ensuring employees in the finance department know, for example, to confirm any changes to a vendor’s bank information before releasing funds, is key to protecting your organization from falling prey to the increasingly sophisticated BEC landscape.
by Doug Kreitzberg | Nov 5, 2020 | Business Email Compromise, Uncategorized

by Doug Kreitzberg | Aug 28, 2020 | Business Email Compromise, Cybersecurity, social engineering
Last week we wrote about the significant cost of business email compromise (BEC) scams compared to other, more-publicized cyber attacks. Now, the cybersecurity firm Agari has published a report showing a new BEC threat emerging — one that is more sophisticated and more costly than what we have seen in the past.
Business email compromise threats are a form of social engineering scams that have been around for a long time. “Nigerian prince scams,” for example, are what people often think of when they think of these types of attacks. However, as technology and modes of communication have gotten more sophisticated, so too have the scammers. Agari’s new report details the firm’s research on a new gang of BEC scammers based in Russia that call themselves “Cosmic Lynx.”
Unlike most BEC scams that tend to target smaller, more vulnerable organizations, the group behind Cosmic Lynx tends to go after gigantic corporations — most of which are Fortune 500 or Global 2000 companies. While larger organizations are more likely to have more sophisticated cybersecurity protocols in place, that doesn’t mean they can’t be tricked, and the payout for successful scams is significantly larger. The average amount requested through BEC is typically $55,000. Cosmic Lynx, on the other hand, requests $1.27 million on average.
How Does it Work?
While the basic’s of Cosmic Lynx’s BEC attacks are pretty standard, the group uses more advanced technology and social engineering tactics to make their scams more successful.
Typically, Cosmic Lynx uses a “dual impersonation scheme” that mimics indidvuals both within and outside of the target of the scams. Moreover, by manipulating standard email authentication settings and registering domains that imitate common secure email domains (such as secure-mail-gateway[.]cc), the group is able to convincingly spoof their email address and display name to look almost identical to a employees within the targeted business. Acting as the CEO, the group will typically send an email to a Vice President or Managing Director notifying them of a new acquisition and referring the employee to an external legal team to finalize the deal and transfer funds.
Cosmic Lynx will then impersonate the identity of a real lawyer and send the employee an email explaining they are helping to facilitate the payment. Of course, organization receiving the funds is actually a mule account — typically Hong Kong-based — controlled by Cosmic Lynx.
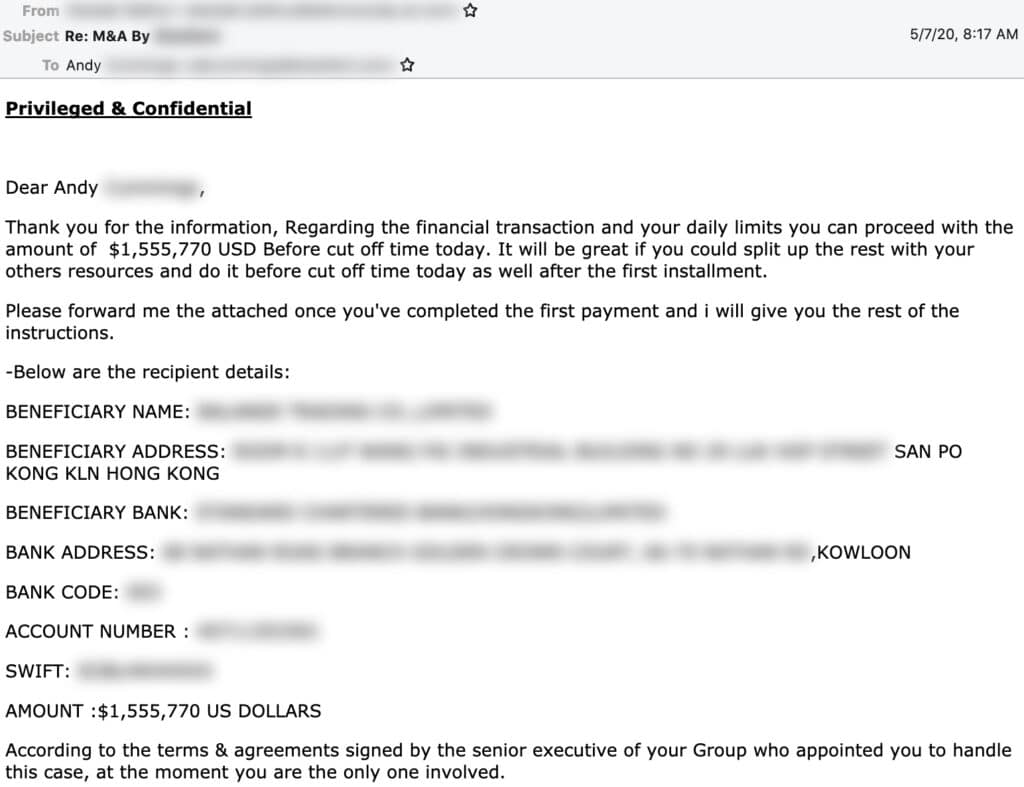
Source: Agari
For now, Cosmic Lynx seems to be the only group carrying this new BEC threat, however it is very likely other groups, seeing the amount Cosmic Lynx is raking in, will begin to follow suit. Simply put, the level of sophistication involved in these scams will require businesses to have more sophisticated protections in place to prevent this new threat. While more advanced email filters may help to detect spoofed email addresses, the most effective method to prevent BEC scams is to have strong policies in place to verify payment requests before releasing funds.

by Doug Kreitzberg | Aug 24, 2020 | Business Email Compromise, ransomware, Risk Management
According to this year’s Cost of a Data Breach Report, the majority of malicious cyber attacks are financially motivated. So, when prioritizing risk, it makes sense to focus on cyber threats that have direct financial implications, such as ransomware and business email compromise (BEC) schemes.
Given the recent rise in ransomware attacks and the targeting of public agencies, it’s pretty likely you’ve seen some news about ransomware within the past year. And while it is certainly important to protect against the possibility of ransomware, that doesn’t mean less-publicized cyber attacks like BEC should be taken any less seriously.
In general, business email compromise involves scammers sending employees an email that looks as if it is coming from a familiar source requesting some sort of payment. Usually, scammers will impersonate frequently used vendors or even CEOs. And these scams can be costly. Last year Nikkei, a Japanese media company, suffered a loss of $29 million when a scammer impersonated a company executive.
In fact, BEC scams have repeated topped the FBI’s annual Internet Crime Report as the costliest form of cyber crime. And, when you compare the costs of BEC and ransomware attacks, it becomes pretty clear which one poses the greater risk.
[table id=1 /]
While FBI’s report shows a sharp increase in ransomware losses in recent years, BEC scams continue to outpace ransomware by a staggering margin. If you were responsible for prioritizing risk activities in your organization, where would you focus? When you follow the money, the answer is pretty obvious. The good news, however, is that a lot of the procedures, guidelines, and training that can be done to prevent BEC can also help ransomware, such as anti-malware software and email authentication. It can be easy to base your cybersecurity processes off of what you see in the headlines, but that won’t always give you an accurate view of your risk profile. It’s essential to conduct regular risk assessments to gain a clear understanding of the biggest threats your organization faces.
by Doug Kreitzberg | Aug 17, 2020 | Business Email Compromise, Cyber Awareness, Phishing
We understand the risks of having our email credentials compromised. If it happens, we know to change our login information as quickly as possible to ensure whoever got in can’t continue to access our emails. The problem, however, is that there is a very simple way for hackers to continue to access the content of your inbox even after you change your password: auto-forwarding. If someone gains access to your email, they can quickly change your configurations to have every single email sent to your inbox forwarded to the hacker’s personal account as well.
The most immediate concern with unauthorized auto-forwarding is the ability for a hacker to view and steal any sensitive or proprietary information sent to your inbox. However the risks associated with this form of attack have far greater ramifications. By setting up auto-forwarding, phishers can carry out reconnaissance efforts in order to carry out more sophisticated social engineering scams in the long-term.
For example, auto-forwarding can help hackers carry out spear phishing attacks — a form of phishing where the scammer tailors phishing emails to target specific individuals. By learning how the target communicates with others and what type of email they are most likely to respond to, hackers can create far more convincing phish and increase the chance that their attack will be a success.
Bad actors can also utilize auto-forwarding to craft highly-sophisticated business email compromise (BEC) attacks. BEC is a form of social engineering in which a scammer impersonates vendors or bosses in order to trick employees into transfering funds to the wrong place. If the scammer is using auto-forward, they may be able to see specific details about projects or services being carried out and gain a better sense of the formatting, tone, and style of invoices or transfer requests This can then be used to create fake invoices for actual services that require payment.
How to protect yourself from unauthorized auto-forwarding
There are, however, a number of steps you and your organizations can take to prevent hackers from setting up auto-forwarding. The most obvious is to prevent access to your email account in the first place. Multi-factor authentication, for example, places an extra line of defense between the hacker and your inbox. However, every organization should also disable or limit users’ ability to set up auto-forwarding. Some email providers allow organizations to block auto-forward by default. Your IT or security team can then manually enable auto-forwarding for specific employee’s when requested for legitimate reasons and for a defined time period.
When it comes to the risks with auto-fowarding, the point is that the more the hackers can learn about your organizations and your employees, the more convincing their future phishing and BEC attacks will be. By putting safeguards in place that help prevent access to email accounts and block auto-forwarding, you can lower the risk that a bad actor will gain information about your organization and carry out sophisticated social engineering attacks.

by Doug Kreitzberg | Aug 5, 2020 | Business Email Compromise, Cyber Awareness, Cybersecurity, Data Breach, Phishing, social engineering
Earlier this week we wrote about the cost of human-factored, malicious cyber attacks. However, there are also other threats that can lead to a malicious attack and data breach. According to this year’s Cost of a Data Breach Report, the stolen or compromised credentials tied for the most frequent cause of malicious data breaches, and took the lead as the most costly form of malicious breach.
The root cause of compromised credentials varies. In some cases, stolen credentials are also related to human-factored social engineering scams such as phishing or business email compromise attacks. In other cases, your login information may have been stolen in a previous breach of online services you may use. Hackers will often sell that data on the dark web, where bad actors can then use the data to carry out new attacks.
Whatever the cause, the threat is real and costly. According to the report, compromised credentials accounted for 1 out of every 5 — or 19% of — reported malicious data breaches. That makes this form of attack tied with cloud misconfiguration as the most frequent cause of a malicious breach. However, stolen credentials tend to cost far more than any other cause of malicious breach. According to the report, the average cost of a breach caused by compromised credentials is $4.77 million — costing businesses nearly $1 million more than other forms of attack.
Given the frequency of data breaches caused by compromised credentials, individuals and businesses alike need to be paying closer attention to how they store, share, and use their login information. Luckily, there are a number of pretty simple steps anyone can take to protect their credentials. Here are just a few:
Password Managers
There are now a variety of password managers that can vastly improve your password strength and will help stop you from using the same or similar passwords for every account. In my cases, they can be installed as a browser extension and phone app and will automatically save your credentials when creating an account. Not only are password managers an extremely useful security tool, they are an incredible convenient tool for a time when we all have hundreds of different accounts.
Multi-Factor Authentication
Another important and easy to use tool is multi-factor authentication (MFA), in which you are sent a code after logging in to verify your account. So, even if someone stole your login credentials, they still won’t be able to access your account without a code. While best practice would be to use MFA for any account offers the feature, everyone should at the very least use it for accounts that contain personal or sensitive, such as online bank accounts, social media accounts, and email.
Check Past Compromises
In order to ensure your information is protected, it’s important to know if your credentials have ever been exposed in previous data breaches. Luckily, there is a site that can tell you exactly that. Have I Been Pwned is a free service created and run by cybersecurity expert Troy Hunt, who keeps a database of information compromised during breaches. User’s can go on and search the data to see if their email address or previously used passwords have ever been involved in those breaches. You can also sign up to receive notifications if your email is ever involved in a breach in the future.
Cyber Awareness Training
Lastly, in order to keep your credentials secure, it’s important that you don’t get tricked into give them away. Social engineering, phishing, and businesses email compromise schemes are all highly frequent — and often successful — ways bad actors will try to gain access to your information. Scammers will send emails or messages pretending to be from a company or official source, then direct you to a fake website where you are asked to fill out information or login to your account. Preventing these scams from working largely depends on your ability to accurately spot them. And, given the increased sophistication of these scams, using a training program specifically designed to teach you how to spot the fakes is very important.







