
by Doug Kreitzberg | Jul 6, 2021 | Business Continuity, Cyber Insurance
The shifting cyber risk landscape over the past eighteen months – especially the explosion of ransomware attacks — has put a spotlight on what businesses and governments are doing about cybersecurity risk and what role does or could cyber insurance play – not only as a risk transfer vehicle, but as an enabler of improved risk management practices. As of early 2021 the total global premiums for cyber insurance have reach over $5 billion, but the truth is cyber insurance is still a very new industry, and the role it can play in mitigating cyber risk is has been an open question for a few years.
However, according to a new report by the UK-based security research institute RUSI, the role of cyber insurance as a risk mitigation tool is still pretty limited. One big challenge is that both issuers and insureds too often view cyber insurance as a replacement for actual cybersecurity policies and procedures. Cyber insurance doesn’t mean that you won’t get hacked just like having fire insurance doesn’t mean your house won’t ever burn down. This challenge has most recently been playing out with questions surrounding ransomware payments. Today, many cyber insurance policies include payments for ransom demands. However, this raises the concern that such practices are actually fueling the recent spike in ransomware attacks. In fact, some evidence suggests ransomware attackers are specifically targeting companies with cyber insurance and tailor their demands to the high-end of what those policies will cover.
That said, cyber insurance still has a role to play — but it doesn’t replace the other value chains within the broader risk mitigation process . Like with most insurance, it’s not designed to prevent or eliminate risk, but rather to transfer risk as a last line of defense. In the RUSI report, many of the experts interviewed cite post-incident services as one of the main benefits of having cyber insurance. From incident response to forensic analysis, cyber insurance can be extremely useful for maintaining business continuity following a cyber incident. This is even more important for small businesses who might not have internal teams and the expertise to carry out a post-incident response swiftly and effectively. However, there is a lot more to cyber security than how you respond to an incident. As RUSI’s report points out, right now cyber insurance is most effective as a tool for cyber resilience, but not risk mitigation.
What is important to understand is the need to properly place cyber insurance within your larger risk governance strategy. Cyber risk management is like putting together a puzzle with various shapes and sizes. From performing informed risk assessments, to maintaining strong systems controls, to creating a culture that values cybersecurity, there is a lot of factors that need to be pieced together in a way that aligns with your business context, strategy, and goals. Effective risk management includes a value change of activities and partners, including insurance, but relying on insurance along is not enough.

by Doug Kreitzberg | Dec 28, 2020 | Business Continuity, Cybersecurity
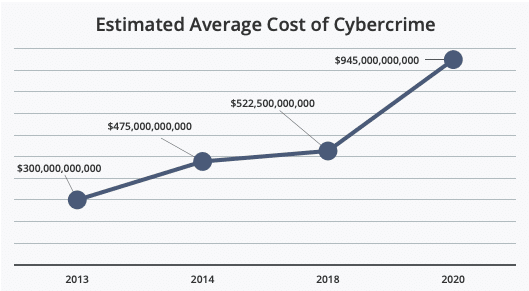
Earlier this year we wrote about the fact that cyber attacks cost businesses millions of dollars per incident. But what about the cost of cybercrime on larger scale? This month, McAfee released a new report analyzing at the cost of cybercrime globally, and the findings are staggering.
The most startling news from the report is the jump in the overall cost of cybercrime globally. Between 2018 and 2020, McAfee found a nearly 50% increase in average global cost. Now, the estimated global cost of cybercrime is $945 billion — more than 1% of the global GDP.
Source: McAfee
Just as startling, however, is that the report found a myriad of additional damages organizations face after a cyber incident beyond direct financial costs. In their report, McAfee found that 92% of organizations surveyed identified “hidden costs” that effected them beyond direct monetary losses. These hidden costs can have long terms effects on an organization’s productivity and ability to prevent future attacks.
One of the main hidden costs the report covers is the “damage to company performance” after a cyber incident. These damages, according to the report, is primarily related to a loss in productivity and lost work hours as businesses attempt to recover from an attack — usually because system downtime and disruptions to normal operations. While these losses might be, to some extent, inevitable following an attack, McAfee’s report found that organizations routinely neglect one essential aspect of cybersecurity: communication within the organizations.
We’ve talked before about the importance of creating an incident response plan, but without communication and cooperation between all areas of an organization, these plans won’t be all that effective. According to the report, IT decision makers think some departments aren’t ever made aware that a cyber incident even happened. The breakdown in communication is especially damaging between IT and business leadership. “IT and line-of-business (LOB) decision makers,” the report says, “have different understandings of what, why, and how a company or government agency is experiencing an IT security incident.” In fact, the lack of communication goes so far as whether or not there is even a response plan at all. The report found that, in general, business leadership often believe there is a response plan in place when there isn’t one.
This lack of communication also extends to the nature and scope of an organization’s cyber risk. The report noted a significant lack of organization-wide understand of cyber risk, which, the report states, “makes companies and agencies vulnerable to social engineering tactics. Once a user is hacked, they do not always recognize the problem in time to stop the spread of malware.”
While there will almost always be disruptions and hidden costs following a cyber incident, McAfee’s report seems to indicate many of these losses are self-inflicted. The report shows that the most common change organizations make after a cyber incident is investment in new security software. And, while technical safeguards are certainly necessary, they are far from sufficient. Instead, organizations need to begin investing in policies and procedures that ensure organization-wide communication, knowledge, and response to cyber risk and incidents.

by Doug Kreitzberg | Dec 23, 2020 | Business Continuity, Facebook, Privacy, small business
Ever since Apple announced new privacy features included in the release of OS 14, Facebook has waged a war against the company, arguing that these new features will adversely effect small businesses and their ability to advertise online. What makes these attacks so “laughable” is not just Facebook’s disingenuous posturing as the protector of small businesses, but that their campaign against Apple suggests privacy and business are fundamentally opposed to each other. This is just plain wrong. We’ve said it before and we’ll say is again: Privacy is good for business.
In June, Apple announced that their new mobile operating system, OS 14, would include a feature called “AppTrackingTransparency” that requires apps to seek permission from users before tracking activity between others apps and websites. This feature is a big step towards prioritizing user control of data and the right to privacy. However, in the months following Apple’s announcement, Facebook has waged a campaign against Apple and their new privacy feature. In a blog post earlier this month, Faceboook claims that “Apple’s policy will make it much harder for small businesses to reach their target audience, which will limit their growth and their ability to compete with big companies.”
And Facebook didn’t stop there. They even took out full-page ads in the New York Times, Wall Street Journal and Washington Post to make their point.
Given the fact that Facebook is currently being sued by more than 40 states for antitrust violations, there is some pretty heavy irony in the company’s stance as the protector of small business. Yet, this is only scratches the surface of what Facebook gets wrong in their attacks against Apple’s privacy features.
While targeted online adverting has been heralded as a more effective way for business to reach new audiences and start turning a profit, the groups that benefit the most from these highly-targeted ad practices are in reality gigantic data brokers. In response to Facebook’s attacks, Apple released a letter, saying that “the current data arms race primarily benefits big businesses with big data sets.”
The privacy advocacy non-profit, Electronic Frontier Foundation, reenforced Apple’s point and called Facebook’s claims “laughable.” Start ups and small business, used to be able to support themselves by running ads on their website or app. Now, however, nearly the entire online advertising ecosystem is controlled by companies like Facebook and Google, who not only distribute ads across platforms and services, but also collect, analyze and sell the data gained through these ads. Because these companies have a strangle hold on the market, they also rake in the majority of the profits. A study by The Association of National Advertisers found that publishers only get back between 30 and 40 cents of every dollar spent on ads. The rest, the EFF says, “goes to third-party data brokers [like Facebook and Google] who keep the lights on by exploiting your information, and not to small businesses trying to work within a broken system to reach their customers.”
Because tech giants such as Facebook have overwhelming control on online advertising practices, small businesses that want to run ads have no choice but to use highly-invasive targeting methods that end up benefitting Facebook more than these small businesses. Facebook’s claim that their crusade against Apple’s new privacy features is meant to help small businesses just simply doesn’t hold water. Instead, Facebook has a vested interest in maintaining the idea that privacy and business are fundamentally opposed to one another because that position suits their business model.
At the end of the day, the problem facing small business is not about privacy. The problem is the fundamental imbalance between a handful of gigantic tech companies and everyone else. The move by Apple to ensure all apps are playing by the same rules and protecting the privacy of their users is a good step towards leveling the playing field and thereby actually helping small business grow.
This also shows the potential benefits of a federal, baseline privacy regulation. Currently, U.S. privacy regulations are enacted and enforced on the state level, which, while a step in the right direction, can end up staggering business growth as organizations attempt to navigate various regulations with different levels of requirements. In fact, last year CEOs sent a letter to congress urging the government to put in place federal privacy regulations, saying that “as the regulatory landscape becomes increasingly fragmented and more complex, U.S. innovation and global competitiveness in the digital economy are threatened” and that “innovation thrives under clearly defined and consistently applied rules.”
Lastly, we recently wrote about how consumers are more willing to pay more for services that don’t collect excessive amounts of data on their users.This suggests that surveillance advertising and predatory tracking do not build customers, they build transactions. Apple’s new privacy features open up a space for business to use privacy-by-design principles in their advertising and services, providing a channel for those customers that place a value on their privacy.
Privacy is not bad for business, it’s only bad for business models like Facebook’s. By leveling the playing field and providing a space for new, privacy-minded business models to proliferate, we may start to see more organizations realize that privacy and business are actually quite compatible.

by Doug Kreitzberg | Sep 14, 2020 | Business Continuity, Cybersecurity
Like everyone today, our elections officials have to grapple with technological changes. And with those changes comes emerging security concerns. Take the 2020 democratic Iowa caucus, for example. The Iowa Democratic Party decided to use a new app to record results of the caucus that ended up causing a myriad of problems, delaying the results and sparking a controversy about the party’s use of the app. As more states begin to digitalize the election process, election security has become a topic of national concern. Of course, the stakes of an incident is probably not as high for a business as, say, protecting the democratic process. However, when looking at a case with such high stakes, incidents in our elections can clarify what we expect not only from our government but also what consumers expect from companies, and what organizations need to be taking seriously. Here are just three areas from which business can learn from the issues surrounding election security.
Trust
The first thing that business and election security officials have in common is the need to maintain public trust. One of the biggest concerns with digitalizing our elections is, if something goes wrong with the technology, it may harm the public’s trust in the voting process. This was certainly the case in Iowa this year. Despite the party’s assurance that even with the app down the results of the caucus could be accurately counted, disinformation and confusion quickly spread online.
It’s not difficult to see how businesses can apply these election security concerns to their organizations. A public security issue with a produce or service could severely impact a business’s reputation and can be extremely difficult to repair. Consumers may feel like their privacy could be at risk and that your business doesn’t have their best interest in mind. To combat this, besides actively securing consumer data, businesses should be as transparent as possible with consumers about the organization’s cybersecurity efforts.
Management
Soon after the Iowa caucus, it become abundantly clear that the app developers and the Iowa Democratic Party made a number of mistakes that lead to the problems on caucus night. For example, before the night of the caucus, the app was only tested internally, with no external review. The IDP even declined an offer from Homeland Security to review the app before roll out. Developers also didn’t have time to get the app approved through app stores, so required users to download the app through testing software, effectively by-passing the need to meet the security requirements from app stores.
The list of ways that the rollout was mismanaged goes on and on. However, this only highlights the need for business management to be involved in ensuring proper cybersecurity best practices are followed through the entire product lifecycle, from initial development, to implementation, and on going maintenance.
Response Planning
Businesses should also look at how election security officials respond—or, perhaps more accurately, don’t respond— to issues that arise. Without a proper response plan in place, problems could worsen and cause enough confusion to allow disinformation about the issue to spread. And that’s exactly what happened in Iowa. As the problem with the Iowa caucus came to light, instead of deploying a carefully planned incident response, the whole night turned into chaos and confusion, as caucus leaders sat on hold for hours to deliver results or even text pictures of their tallies to party headquarters.
This example shows just how necessary it is for businesses to have a proper incident response plan in place. This should involve sitting down with business leaders, IT staff, and other relevant employees to write out a detailed response for every incident that could arise. With a plan in place, businesses should also conduct regular incident response simulations, by asking the response team to test their plan for each possible incident. Responding to an incident quickly and efficiently will not only help limit the impact of the issue, but could help show regulatory bodies your proactive stance to cyber incidents, and even save your business money.
With the general election looming, election security officials are working hard to ensure no problems arise on election day. Hopefully, come November there won’t be any lessons for businesses to learn from.

by Doug Kreitzberg | Sep 11, 2020 | Business Continuity, Cybersecurity, Risk Culture, Risk Management
Today business leaders are rightfully concerned about mitigating their organization’s cyber risks. To address this concern, many businesses have begun to hire individfuals responsible for cybersecurity and even hiring Chief Information Security Officers (CISOs) to provide security leadership at the executive level. But unfortunately, old habits die hard. Instead of integrating the cybersecurity team or the CISO into both cybersecurity and business conversations, many of these security leaders have become siloed from broader business strategy and goals. Of course, this also leaves the executive team under-informed about the nature and scope of their organization’s cyber risk profile.
One of the main tenants of a new security principle, cyber resiliency, stresses the need to integrate approaches to security and business in order for either side to succeed. In fact, organizations should even stop thinking of business and security as two opposing side of an equation and instead learn to see and promote the integration of each with the other. However, this will require both security experts and businesses leaders to put in some work.
Business-Aligned Security Leaders
A recent report by Forrester found that just four out of ten security leaders can answer the question, “How secure/at risk are we?” and less than half frequently consult business leaders before developing security strategies. This, to put it lightly, is a big problem. If security leaders are just focused on implementing and maintaining technical controls, they end up missing the bigger picture of the risk culture that surrounds those controls. It is vitally important for security teams to understand an organization’s business-critical assets and work with leadership to develop a risk mitigation plan that prioritizes those assets.
Cybersecurity teams also need to be able to communicate their needs to business leadership. According to the Forrester report, more than half of security leaders lack adequate skills in benchmarking their security programs. In order to integrate cybersecurity and business needs, security teams need to develop benchmarking and risk reports that they can properly communicate to business executives. Taking a more business-oriented approach to security can also help security leaders advocate for the funds they need to reduce risk.
Cyber-Aligned Business Leaders
Of course, in order for security leaders to effectively integrate business strategy into overall cybersecurity goals, the business executives and board members need to regularly meet and communicate with their security team. To ensure this happens, it’s important for board members to assume ultimate responsibility for oversight of the organization’s security and to integrate cybersecurity discussions into the overall business strategy, risk management, and budgeting. It may even be a good idea to require cybersecurity training for all board members to ensure everyone has a proper understanding of the current threat landscape and regulations.
With a focus on outcomes, training, and a security team able to communicate benchmarks and risk reports, board members will be in a position to properly define the organization’s cyber risk tolerance that is consistent with business strategy and current cybersecurity controls. Board members and executives teams must ensure the organization’s risk appetite is communicated throughout all levels of the organization and that they create a culture that reflects the cybersecurity and business interests of the organization. Many of these recommendations are included in a white paper from the World Economic Forum that details 10 essential principles and tools for boards to better integrate cyber resiliency with overall business strategy.
Today, most organizations understand the importance of maintaining an effective cybersecurity program. However, not many businesses are recognizing the interdependence of cybersecurity and business interests. And it’s a two way street. Both cybersecurity leaders and business executive and board members need to be mindful about taking a more holistic approach to cybersecurity and business for either to be effective.

by Doug Kreitzberg | Jul 6, 2020 | Business Continuity, Cybersecurity, Data Breach
Cybersecurity tools are important for lowering the risk of a data breach. However, if those tools are put in place without considering business outcomes, it can harm organizational goals and even, in some cases, cost lives. In the healthcare industry, for example, steps taken to recover from a data breach can lead to a drop in the quality of care. However, no matter the industry, if cybersecurity tools and businesses goals are not aligned, there will almost always be negative consequences for that business.
A study published last year in the Health Services Research Journal found that after a hospital experienced a data breach there was, on average, an additional 36 deaths from heart attacks per 10,000 patients. One of the main factors that contributes to this is a delay in treatment because of new security policies following a breach. Common tools used after a breach include additional sign-in measures such as multi-factor authentication, or automatic logout after a period of inactivity. So if someone comes into a hospital with chest pain, for example, these extra security measures delay the ability for doctors and nurses to register the patient and access health records. This is especially important to consider now, given that hacks against the healthcare industry have risen since the COVID-19 pandemic began.
Of course, this isn’t to say that there shouldn’t be any additional security measures in place after a breach Instead, the point is that it is important to align cybersecurity processes with overall business goals — even when the stakes aren’t as high as saving a life. The key is to begin with your desired business outcomes and look at the cybersecurity risks that can negatively impact those goals. Then, only once you know your specific risks do you design or apply tools that limit those risks without negatively impacting the business. This requires strong governance and communication between IT and business leadership. Failure to focus on the interplay between cybersecurity and business goals both weakens the security posture and weakens business outcomes. And that’s not a prescription for a healthy strategy.






