by Doug Kreitzberg | Apr 29, 2020 | Coronavirus, Privacy
As the COVID-19 pandemic continues, the world has turned to the tech industry to help mitigate the spread of the virus and, eventually, help transition out of lockdown. Earlier this month, Apple and Google announced that they are working together to build contact-tracing technology that will automatically notify users if they have been in proximity to someone who has tested positive for COVID-19. However, reports show that there is a severe lack of evidence to show that these technologies can accurately report infection data. Additionally, the question arises as to the efficacy of these types of apps to effectively assist the marginal populations where the disease seems to have the largest impact. Combined with the invasion of privacy that this involves, the U.S. needs to more seriously interrogate whether or not the potential rewards of app-based contact tracing outweigh the obvious—and potentially long term— risks involved.
First among the concerns is the potential for the information collected to be used to identify and target individuals. For example, in South Korea, some have used the information collected through digital contact tracing to dox and harass infected individuals online. Some experts fear that the collected data could also be used as a surveillance system to restrict people’s movement through monitored quarantine, “effectively subjecting them to home confinement without trial, appeal or any semblance of due process.” Such tactics have already been used in Israel.
Apple and Google have taken some steps to mitigate the concerns over privacy, claiming they are developing their contact tracing tools with user privacy in mind. According to Apple, the tool will be opt-in, meaning contact tracing is turned off by default on all phones. They have also enhanced their encryption technology to ensure that any information collected by the tool cannot be used to identify users, and promise to dismantle the entire system once the crisis is over.
Risk
Apple and Google are not using the phrase “contact tracing” for their tool, instead branding it as “exposure notification.” However, changing the name to sound less invasive doesn’t do anything to ensure privacy. And despite the steps Apple and Google are taking to make their tool more private, there are still serious short and long term privacy risks involved.
In a letter sent to Apple and Google, Senator Josh Hawley warns that the impact this technology could have on privacy “raises serious concern.” Despite the steps the companies have taken to anonymize the data, Senator Hawley points out that by comparing de-identified data with other data sets, individuals can be re-identified with ease. This could potentially create an “extraordinarily precise mechanism for surveillance.”
Senator Hawley also questions Apple and Google’s commitment to delete the program after the crisis comes to an end. Many privacy experts have echoed these concerns, worrying what impact these expanded surveillance systems will have in the long term. There is plenty of precedent to suggest that relaxing privacy expectations now will change individual rights far into the future. The “temporary” surveillance program enacted after 9/11, for example, is still in effect today and was even renewed last month by the Senate.
Reward?
Contact tracing is often heralded as a successful method to limit the spread of a virus. However, a review published by a UK-based research institute shows that there is simply not enough evidence to be confident in the effectiveness of using technology to conduct contact tracing. The report highlights the technical limitations involved in accurately detecting contact and distance. Because of these limitations, this technology might lead to a high number of false positives and negatives. What’s more, app-based contact tracing is inherently vulnerable to fraud and cyberattack. The report specifically worries about the potential for “people using multiple devices, false reports of infection, [and] denial of service attacks by adversarial actors.”
Technical limitations aside, the effectiveness of digital contact tracing also requires both large compliance rate and a high level of public trust and confidence in this technology. Nothing suggests Apple and Google can guarantee either of these requirements. The lack of evidence showing the effectiveness of digital contact tracing puts into question the use of such technology at the cost serious privacy risks to individuals.
If we want to appropriately engage technology, we should determine the scope of the problem with an eye towards assisting the most vulnerable populations first and at the same time ensure that the perceived outcomes can be obtained in a privacy perserving manner. Governments need to lay out strict plans for oversight and regulation, coupled with independent review. Before comprising individual rights and privacy, the U.S. needs to thoroughly asses the effectiveness of this technology while implementing strict and enforceable safeguards to limit the scope and length of the program. Absent that, any further intrusion into our lives, especially if the technology is not effective, will be irreversible. In this case, the cure may well be worse than the disease.

by Doug Kreitzberg | Apr 23, 2020 | Coronavirus, Data Breach
This week, reports surfaced that the Small Business Association’s COVID-19 loan program experienced an unintentional data breach last month, leaving the personal information of up to 8,000 applicants temporarily exposed. This is just the latest in a long line of COVID-19 cyber-attacks and exposures since the pandemic began.
The effected program is the SBA’s long-standing Economic Injury Disaster Loan program (EIDL), which congress recently expanded to help small businesses effected by the COVID-19 crisis. The EIDL is separate from the new Paycheck Protection Program, which is also run by the SBA.
According to a letter sent to affected applicants, on March 25th the SBA discovered that the application system exposed personal information to other applicants using the system. The information potentially exposed include names, addresses, phone numbers, birth dates, email addresses, citizenship status, insurance information, and even social security numbers of applicants
According to the SBA, upon discovering the issues they “immediately disabled the impacted portion of the website, addressed the issue, and relaunched the application portal.” All businesses affected by the COVID-19 loan program breach were eventually notified by the SBA and offered a year of free credit monitoring.
A number of recent examples show that the severe economic impact of the pandemic has left the SBA scrambling. Typically, the SBA is meant to issue funds within three days of receiving an application. However, with more than 3 million applications flooding in, some have had to wait weeks for relief.
The unprecedented number of applications filed, coupled with the fact the SBA is smallest major federal agency — suffering a 11% funding cut in the last budget proposal — likely contributed to the accidental exposure of applicant data. However, whether accidental or not, a data breach is still a data breach. It’s important that all organizations take the time to ensure their systems and data remain secure, and that mistakes do not lead to more work and confusing during a time of crisis.

by Doug Kreitzberg | Apr 22, 2020 | Coronavirus, Data Breach
The current onslaught of cyberattacks related to the COVID-19 pandemic continued this week. Tuesday night, reports surfaced that attackers publicized over 25,000 emails and passwords from the World Health Organization, The Gates Foundation, and other organizations working to fight the current COVID-19 pandemic. What’s more, this new data dump starkly shows how easily data breaches related to COVID-19 can fuel disinformation campaigns.
The sensitive information was initially posted online over the course of Sunday and Monday, and quickly spread to various corners of the internet often frequently by right-wing extremists. These groups rapidly used the breached data to create widespread harassment and disinformation campaigns about the COVID-19 pandemic. One such group posted the emails and passwords to their twitter page and pushed a conspiracy theory that the information “confirmed that SARS-Co-V-2 was in fact artificially spliced with HIV.”
A significant portion of the data may actually be out of date and from previous data breaches. In a statement to The Washington Post, The Gates Foundation said they “don’t currently have an indication of a data breach at the foundation.” Reporting by Motherboard also found that much of the data involved matches information stolen in previous data breaches. This indicates that at least some of the passwords circulating are not linked to the organizations’ internal systems unless employees are reusing passwords.
However, some of the information does appear to be authentic. Cybersecurity expert Robert Potter was able to use some of the data to access WHO’s internal computer systems and said that the information appeared to be linked to a 2016 breach of WHO’s network. Potter also noted a trend of disturbingly poor password security at WHO. “Forty-eight people have ‘password’ as their password,” while others simply used their own first names or “changeme.”
Consequences
Whether the majority of the information is accurate or not, it does not change the fact that the alleged breach has successfully fueled more disinformation campaigns about the COVID-19 pandemic. In the past few weeks, many right-wing extremist groups have used disinformation about the pandemic to spread further fear, confusion in the hopes of seeding more chaos.
This episode starkly shows how data breaches can cause damage beyond the exposure of sensitive information. They can also be weaponized to spread disinformation and even lead to political attacks.

by Doug Kreitzberg | Apr 15, 2020 | Coronavirus, social engineering
Since the beginning of the COVID-19 pandemic, we’ve seen a lot scammers using the pandemic to their advantage. From attacks on the health care industry, to phishing campaigns impersonating the CARES Act small business loan program, online scammers are out in full force to exploit of our fear and confusion. So it’s not surprising to see the Federal Trade Commission confirm that COVID-19 scams are on the rise.
But what is surprising is that those scams have already resulted in $13.44 million in fraud loss since January. This morning the FTC released updated data relating to COVID-19 scams reported to their agency. Here are a few key points from the new data:
- Since January, there are been over 18,000 reports made to the FTC about COVID-19 related scams.
- 46% of scams reported resulted in the victim losing money.
- The most common form of fraud involve scammers impersonating travel and vacation companies such as airlines and hotels. Online shopping companies are also a large source of fraud. Many report that fake businesses are selling high-demand cleaning and medical products that simply never arrive after you pay for them.
- A lot of scammers are also pretending to be the government. In many cases, this involves asking the victim to report personal and financial information to receive their stimulus check.
- Robocalls are back on the rise. Last year, we finally started to see a decline in the number of robocalls. However, those numbers are starting to rise again as scammers use the COVID-19 crisis to commit fraud or illegally gain personal information.
What You Should do
While we are certainly going through an unprecedented and confusing time, it’s important that you stay alert online for COVID-19 scams. If a person or businesses calls, texts, or emails you asking for money or personal details, make sure you know exactly who you are talking to. Here are a few tips to stay safe online:
- If you ever receive a random call claiming to be from the government asking for payment, hang up. The government will never call out of the blue to ask for financial or other personal information.
- When doing online shopping, google reviews of the company first to see if people are getting their products.
- If you get an email from a known company or friend asking or money, look carefully at the email address and URL in the email to make sure they are legitimate.
- If you aren’t sure if something is a scam or not, try googling it or even looking on Twitter. In many cases, scammers will send the same message out to a lot of people, so you may find some helpful stranger warning you not to fall for it.
Above all else, it’s important to practice good digital awareness everywhere online. Be skeptical of what you are seeing and reading. Follow up. Look for others online who can confirm what you’re seeing is real. Scammers rely on us making split decisions, so just taking an extra minute to confirm something is real could end up saving you money.

by Doug Kreitzberg | Apr 8, 2020 | Coronavirus, Privacy
Much has been written about the security and privacy issues with the Zoom videoconferencing application. What may be written more about over the next few months (and in numerous case studies) is how Zoom is responding to those issues.
To begin, the CEO, Eric Yuan, has apologized for Zoom’s prior lack of focus on privacy. Next, his team has stopped all development projects to focus exclusively on security and privacy issues. In addition, he has hired Alex Stamos to be Zoom’s privacy and security advisor as well as has recruited top Chief Security Officers from around the world to serve on an advisory board.
With a user base which has more than doubled since the beginning of the year, Zoom has benefited greatly from the WFH global environment. It is incredible that it has been able to sustain its operability during this growth. But it’s perhaps more impressive that the company, and its CEO in particular, is focusing seriously and aggressively on privacy. This is particularly notable in an era that is unfortunately also fraught with profiteering, scamming and passing the buck.
It hopefully is a wake up call for any company to take it’s privacy issues seriously and to recognize that by doing so, you are not only securing public trust, you are creating brand value.
In 1982, Tylenol responded to its own crisis, when some of its products were tampered leading to poisoning, by pulling every bottle off the shelves and owning the issue. Since then, their response has been a PR crisis case study.
I think Zoom is on its way to becoming a case study as well.
by Doug Kreitzberg | Apr 2, 2020 | Coronavirus, Human Factor, Phishing
Online scammers continue to use the COVID-19 crisis to their advantage. We have already seen phishing campaigns against the healthcare industry. The newest target? Small businesses. This week, the Small Business Administration Office of the Inspector General (SBA OIG) sent out a letter warning of an increase of phishing scams related to the new CARES Act targeting business owners.
CARES Act Loan Scams
The uptick in phishing scams imitating the SBA is primarily linked to the recent stimulus bill the government passed in response to the ongoing COVID-19 crisis. The bill, called the CARES Act, includes $350 billion in loans for small businesses. Given the current crisis, many businesses are eager to apply for loans, opening the door to new forms of phishing scams.
In addition, the scale and unprecedented nature of the loan program allows phishers to capitalize on the confusion surrounding the loan services. Last year, the SBA gave out a total of $28 billion, but now has to create a system to provide roughly 12 times that amount over the course of a few months. In order to help with the process, congress allowed the SBA to expand their list of loan venders. While this may help speed up the process, banks with no prior experience with SBA loan programs will now be distributing funds. Speeding up the loan process will help certainly ease the pain of many small businesses, but it also opens the room for errors, errors that scammers can use for personal gain.
What to Look For
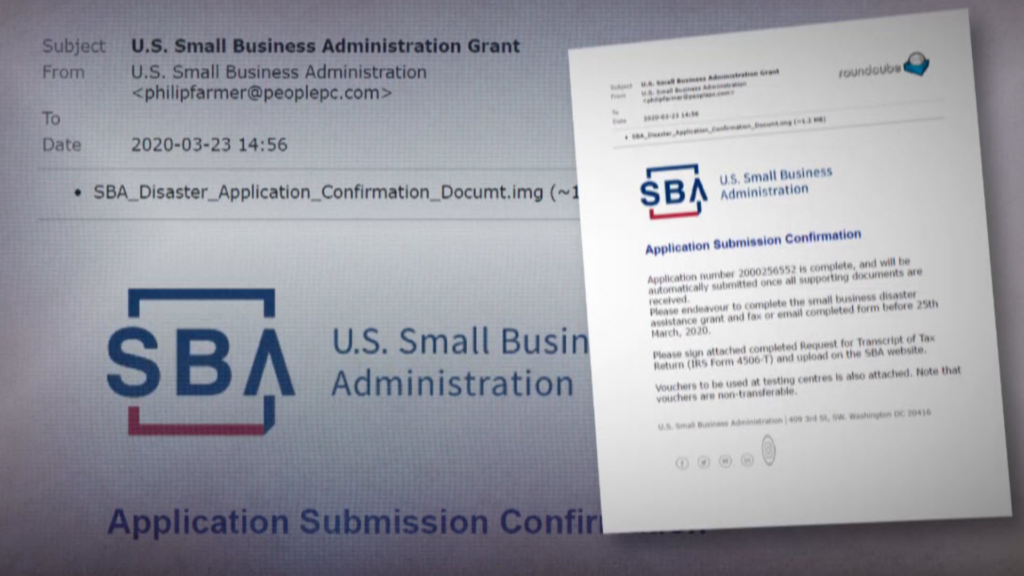
Business owners are already seeing this happen. A small businesses owner recently applied for a loan under the CARES Act to help keep her business running. Shortly after filing her application, her husband received an email stating they would need to fill out and return a tax statement to complete their application.
The email included the SBA logo and looked legitimate. However, on closer inspection, she realized the account number listed in the email did not match the one she received when applying for the loan, and the email address was not from a SBA email account.
Breathe in, Breathe O-U-T
This business owner was savvy enough to not fall for the scam, but others are likely to be tricked into handing over sensitive information or paying money to online scammers. In order to protect people against phishing campaigns, we recommend what we call the Breathe O-U-T Process:
- When you first open an email, first, take a Breath. That’s enough to get started because it acts as a pattern interrupt in automatic thinking and clicking (that leads to people biting the bait).
- Next, Observe the sender. Do you know the sender? Does their email address match who they say they are? Have you communicated with this sender before?
- Then, check Urls and attachments. Hover over the links to see if the URL looks legitimate. Be wary of zip files or strange attachments. If you aren’t sure if a URL is legitimate or not, just go to google and search for the page there instead.
- Finally, take the Time to review the message. Is it relevant? Does it seem too urgent? Does the information match what you already know? How’s the spelling? Be wary of any email which tries too hard to create a sense of urgency. In addition, phish are notoriously known for poor spelling and grammar. While we don’t all write as well as our fourth grade teacher, be careful when you see a lot of “missteaks”.
We’re living through strange and confusing times, and there are people out there who will use that to their advantage. Just taking a few extra minutes to make sure an email is legitimate could help save you a lot of extra time, worry, and money — none of which we can spare these days.
If you want to learn more about phishing scams and how to protect yourself, we are now offering the first month of our cyber awareness course entirely free. Just click here to sign up and get started.