by Doug Kreitzberg | Mar 26, 2021 | Coronavirus, Cyber Awareness, Misinformation
We’ve written before about how the disruption and confusion of the COVID-19 pandemic has caused an uptick in phishing and disinformation campaigns. Yet, there is another dimension to this that is just beginning to become clear: how the isolation of remote work helps to create the conditions necessary for disinformation to take root.
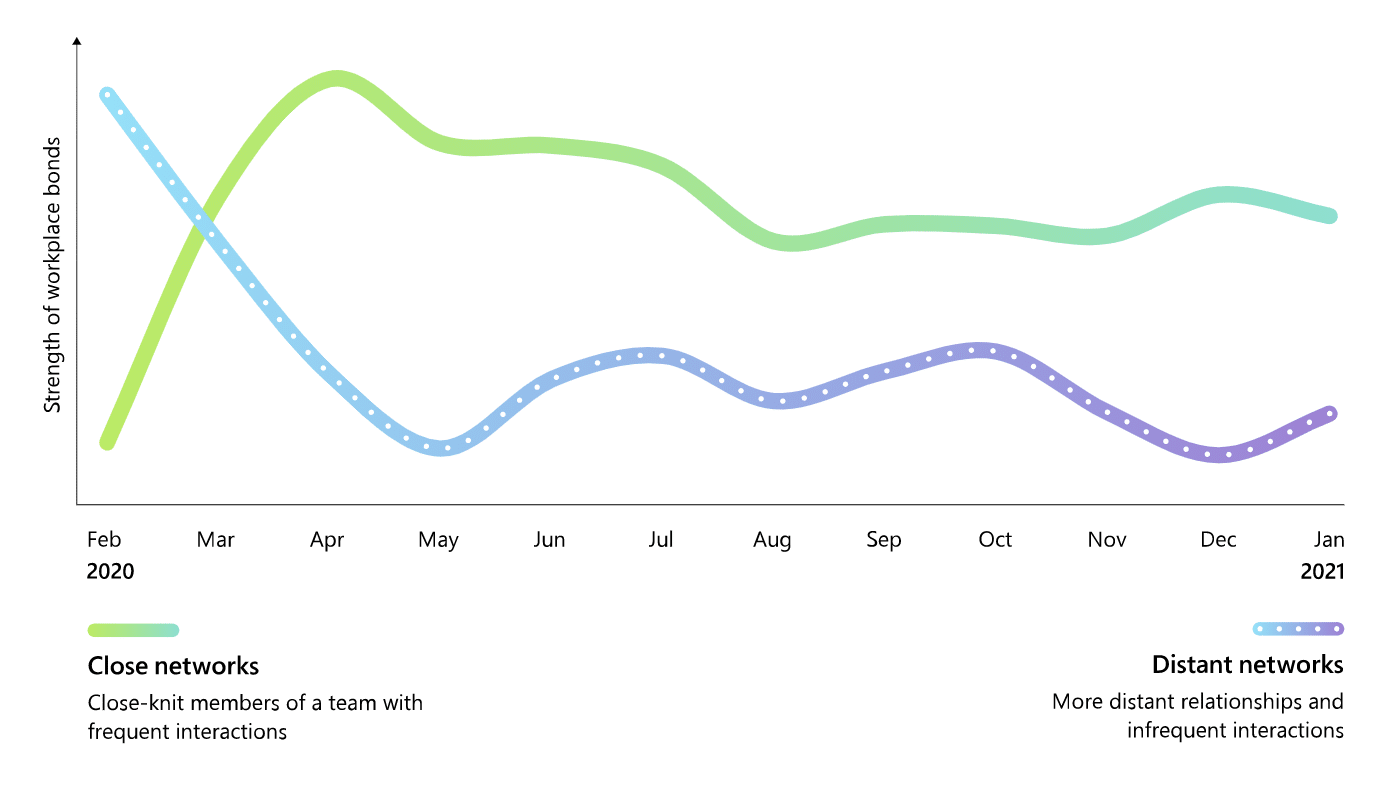
In a report on the impacts of remote and hybrid work on employees, Microsoft highlights how remote work has shrunk our networks. Despite the ability to use video services like Zoom and Microsoft Teams to collaborate with others across the globe, the data reveals that remote work has actually caused us to consolidate our interactions to just those we work closely with, and far less with our extend networks. The result is that employees and teams have become siloed, creating a sort of echo chamber in which new and diverse perspectives are lost. According to Dr. Nancy Baym, Senior Principal Researcher at Microsoft, when are networks shrink, “it’s harder for new ideas to get in and groupthink becomes a serious possibility.”
The gap between interactions with our close network and our distant network created by remote work doesn’t just stifle innovation, it’s also what creates the conditions necessary for disinformation to thrive. When we are only exposed to information and perspectives that are familiar to us, it becomes harder and harder to question what we are being presented. If, for example, we are in a network of people who all believe Elvis is still alive, without exposure to other people who think Elvis in fact isn’t alive we would probably just assume there isn’t any reason to question what those around us are telling us.
The point is, without actively immersing ourselves within networks with differing perspectives, it becomes difficult to exercise our critical thinking abilities and make informed decisions about the validity of the information we are seeing. Remote and hybrid work is likely going to stick around long after the pandemic is over, but that doesn’t mean there aren’t steps we can take to ensure we don’t remained siloed within our shrunken networks. In order to combat disinformation within these shrunken networks we can:
1. Play the Contrarian
When being presented with new information, one of the most important ways to ensure we don’t blindly accept something that may not be true is to play the contrarian and take up the opposite point of view. You may ultimately find that the opposite perspective doesn’t make sense, but will help you take a step back from what you are being shown and give you the chance to recognize there may be more to the story than what you are seeing.
2. Engage Others
It may seem obvious, but engaging with opinions and perspectives that are different than what we are accustomed to is essential to breaking free of the type of groupthink that disinformation thrives on. It can also be a lot harder than it sounds. The online media ecosystem isn’t designed to show you a wide range of perspectives. Instead, it’s up to us to take the time to research other points of view and actively seek out others who see things differently.
3. Do a Stress Test
Once you have a better sense of the diversity of perspectives on any given topic, you’re now in a position to use your own critical thinking skills to evaluate what you — and not those around you — think is true. Taking in all sides of an issue, you can then apply a stress test in which you try to disprove each point of view. Which ever perspective seems to hold up the best or is hardest to challenge will give you a good base to make an informed decision about what you think is most legitimate.
From our personal lives to the office, searching for opposite and conflicting perspectives will help build resilience against the effects of disinformation. It can also even help to be more effective at spotting phish and social media campaigns. By looking past the tactics designed to trick us into clicking on a link or giving away information, and taking a few seconds to take a breathe, examine what we are looking at, and stress test the information we are being shown, we can be a lot more confident in our ability to tell the difference between phish and phriend.

by Doug Kreitzberg | Nov 19, 2020 | Artificial Intelligence, Coronavirus, Disinformation, Human Factor, Misinformation, Reputation, social engineering, Social Media
By now, most everyone has heard about the threat of misinformation within our political system. At this point, fake news is old news. However, this doesn’t mean the threat is any less dangerous. In fact, over the last few years misinformation has spread beyond the political world and into the private sector. From a fake news story claiming that Coca-Cola was recalling Dasani water because of a deadly parasite in the bottles, to false reports that an Xbox killed a teenager, more and more businesses are facing online misinformation about their brands, damaging the reputations and financial stability of their organizations. While businesses may not think to take misinformation attacks into account when evaluating the cyber threat landscape, it’s more and more clear misinformation should be a primary concern for organizations. Just as businesses are beginning to understand the importance of being cyber-resilient, organizations need to also have policies in place to stay misinformation-resilient. This means organization need to start taking both a proactive and a reactive stance towards future misinformation attacks.
Perhaps the method of disinformation we are all most familiar with is the use of social media to quickly spread false or sensationalized information about a person or brand. However, there are a number of different guises disinformation can take. Fraudulent domains, for example, can be used to impersonate companies in order to misrepresent brands. Attackers also create copy cat sites that look like your website, but actually contain malware that visitors download when the visit the site. Inside personnel can weaponize digital tools to settle scores or hurt the company’s reputation — the water-cooler rumor mill now can now play out in very public and spreadable online spaces. And finally, attackers can create doctored videos called deep fakes that can create convincing videos of public figures saying things on camera they never actually said. You’ve probably seen deepfakes of politicians like Barak Obama or Nancy Pelosi, but these videos can also be used to impersonate business leadership that are shared online or circulated among staff.
With all of the different ways misinformation attacks can be used against businesses, its clear organizations need to be prepared to stay resilient in the face of any misinformation that appears. Here are 5 steps all organizations should take to build and maintain a misinformation-resilient business:
1. Monitor Social Media and Domains
Employees across various departments of your organization should be constantly keeping their ear to the ground by closely monitoring for any strange or unusual activity by and about your brand. Your marketing and social media team should be regularly keeping an eye on any chatter online about the brand and evaluate the veracity of claims being made, where they originate, and how widespread is the information is being shared.
At the same time, your IT department should be continuously looking for new domains that mention or closely resemble your brand. It’s common for scammers to create domains that impersonate brands in order to spread false information, phish for private information, or just seed confusion. The frequency of domain spoofing has sky-rocketed this year, as bad actors take advantage of the panic and confusion surrounding the COVID-19 pandemic. When it comes to spotting deepfakes, your IT team should invest in software that can detect whether images and recordings have been altered
Across all departments, your organization needs to keep an eye out for any potential misinformation attacks. Departments also need to be in regular communication with each other and with business leadership to evaluate the scope and severity of threats as soon as they appear.
2. Know When You Are Most Vulnerable
Often, scammers behind misinformation attacks are opportunists. They look for big news stories, moments of transition, or when investors will be keep a close eye on an organization in order to create attacks with the biggest impact. Broadcom’s shares plummeted after a fake memorandum from the US Department of Defense claimed an acquisition the company was about to make posed a threat to national security. Organization’s need to stay vigilant for moments that scammer can take advantage of, and prepare a response to any potential attack that could arise.
3. Create and Test a Response Plan
We’ve talked a lot about the importance of having a cybersecurity incident response plan, and the same rule is true for responding to misinformation. Just as with a cybersecurity attack, you shouldn’t wait to figure out a response until after attack has happened. Instead, organizations need to form a team from various levels within the company and create a detailed plan of how to respond to a misinformation campaign before it actually happens. Teams should know what resources will be needed to respond, who internally and externally needs to be notified of the incident, and which team members will respond to which aspect of the incident.
It’s also important to not just create a plan, but to test it as well. Running periodic simulations of a disinformation attack will not only help your team practice their response, but can also show you what areas of the response aren’t working, what wasn’t considered in the initial plan, and what needs to change to make sure your organization’s response runs like clock work when a real attack hits. Depending on the organization, it may make sense to include disinformation attacks within the cybersecurity response plan or to create a new plan and team specifically for disinformation.
4. Train Your Employees
Employees throughout the organizations should also be trained to understand the risks disinformation can pose to the business, and how to effectively spot and report any instances they may come across. Employees need to learn how to question images and videos they see, just as they should be wary links in an email They should be trained on how to quickly respond internally to disinformation originated from other insiders like disgruntled employees, and key personnel need to be trained on how to quickly respond to disinformation in the broader digital space.
5. Act Fast
Putting all of the above steps in place will enable organizations to take swift action again disinformation campaigns. Fake news spreads fast, so an organizations need to act just as quickly. From putting your response plan in motion, to communicating with your social media follow and stake-holders, to contacting social media platforms to have the disinformation content removed all need to happen quickly for your organization to stay ahead of the attack.
It may make sense to think of cybersecurity and misinformation as two completely separate issues, but more and more businesses are finding out that the two are closely intertwined. Phishing attacks rely on disinformation tactics, and fake news uses technical sophistications to make their content more convincing and harder to detect. In order to stay resilient to misinformation, businesses need to incorporate these issues into larger conversations about cybersecurity across all levels and departments of the organization. Preparing now and having a response plan in place can make all the difference in maintaining your business’s reputation when false information about your brand starts making the rounds online.

by Doug Kreitzberg | Jul 29, 2020 | Coronavirus, Identity, small business
Alongside all of the harm the COVID-19 pandemic has caused to our family, friends, and businesses, the unfortunate truth is that hackers and scammers are profiting off of the chaos. From data breaches of government sites, to hacks against the healthcare industry, to COVID-related phishing themes, consumers have reported over $98 million lost in COVID-19 scams since January. What is not included in that number, however, is the dramatic increase in COVID-related ID theft against businesses.
Business ID theft is not a new problem. Dun and Bradstreet, a data analytics company that handles credit checks for many businesses, reported a 100% increase in ID theft against businesses in 2019. This year, however, the problem has grown out of control, with a stunning 258% spike in business identity theft since the beginning of 2020. This is in large part directly related to the COVID-19 pandemic, because scammers will steal business information to illegally gain access to relief funds and loans.
According to reports, there are groups of cyber scammers that target small businesses for ID theft throughout the United States. The groups will start by looking up business records through the Secretary of State website, identity the officers and owners connect to the company, then find corresponding tax ID and social security numbers on the dark web. These groups will then forge official documents with this information and submit them to the Secretary of State with a mailing address that they control. Traditionally, they will use these documents to update profiles on credit monitoring sites, like Dun and Bradstreet, and apply for credit lines with companies like Staples, Home Depot and Office Depot. Now, however, these groups have switched their tactics and are carrying out business ID thefts for COVID-related federal assistance, such as unemployment payments or relief loans for small businesses.
As we’ve wrote about before, hackers and scammers will often take advantage if times of crisis, confusion, and uncertainty in order to make money or seed further chaos. Given the dramatic rise of business ID theft throughout the COVID pandemic, small businesses should take steps to protect themself against this threat. The most effective way to detect and prevent ID theft is to regularly monitor and update your business information. This includes keeping an eye on your financial records and credit lines to spot potential fraudulent activity, as well as checking your business records with the federal and state government. If you spot a any changes your records that you don’t recognize, it’s a likely sign someone is in the process of stealing your business’ identity.
It can be hard to regularly monitor your records and stay vigilant when you are trying to keep your business afloat throughout the pandemic, but this is exactly what scammers are hoping for. You don’t need to be checking your credit report every single day, but it is essential to keep as close an eye as possible on your records to ensure you and your business are protected from fraud.

by Doug Kreitzberg | Jun 26, 2020 | Coronavirus, Human Factor, Phishing
Maybe the biggest misconception about forming new habits is that the biggest factor for success is the motivation to change. We often imagine that as long as we want to make a change in our lives, we have the power to do it. In fact, motivation is actually the least reliable element making behavior changes. The hard truth is that simply wanting to make a change is far from enough.
The reason? Motivation isn’t a static thing, it comes and goes in waves. It’s therefore tough to keep our motivation high enough to lead to lasting behavior change. Take the response to the COVID-19 pandemic, for example. When it appeared in the U.S, we were highly motivated to socially distance. As time went on, however, more and more people started to take risks and go out more. The reason isn’t because the dangers were any less present, but because our motivation to stay inside started to wane. The point is, if the sole component to any behavior change is motivation, once that motivation starts to diminish, so will the new habit.
Of course, we have to at some level want to make a change, but we also have to realize that it’s simply not enough. Instead, we need to rely more on starting with changes that requires the least amount of motivate necessary for it to occur. This is the idea behind BJ Fogg’s Tiny Habits that we wrote about last week. If you want to start reading more, it might be tempting to try reading a chapter or two every day. But more often than not, you’re not going to be motivated to keep that up for long. Instead, if your goal is just to read one paragraph of a day a couple times a day, you’re far more likely to keep up the new habit. Then, over time, you’ll find you need less motivation to read more and more, until you don’t even think about it any more.
This can be a hard pill to swallow. We like to believe that we can do anything we set our minds to, and it’s a little disheartening to think we don’t have as much control over our motivation as we might prefer. When looked at from a different angle, however, understanding this fact allows us to focus on what we can control: setting achievable goals and rewarding ourselves when we met them. Focusing on that rather than our inability to keep our motivation high will lead to more successful behavior change.

by Doug Kreitzberg | May 7, 2020 | Coronavirus, Social Media
The dangers of online disinformation is by now common knowledge, but that hasn’t seemed to stop its spread. The current COVID-19 crisis has highlighted both the pervasiveness of disinformation and the danger it poses to society. We are in a situation where we need to rely on information for our health and safety. Yet, when accurate and false information sit side-by-side online, it is extremely difficult to know what to trust. The Director-General of the World Health Organization recognized this problem as early as February when he said that, alongside the pandemic, we are also fighting an “infodemic.” From articles, videos, and tweets discounting the severity of the virus to full-blown conspiracy theories, COVID-19 disinformation is everywhere.
Despite the steps social media sites have taken to combat disinformation about COVID-19, an Oxford study found that 88% of all false or misleading information about the coronavirus appear on social media sites. Another report found that, out of over 49 million tweets about the virus, nearly 38% contained misleading or manipulated content. The reason is largely because social media sites like Twitter and Facebook are trying to put a Band-Aid on a systemic issue. “They’ve built this whole ecosystem that is all about engagement, allows viral spread, and hasn’t ever put any currency on accuracy,” said Carl Bergstrom, a Professor at the University of Washington. Simply put, the root of disinformation is not just based on the content being shared, but also on the deep-seated practices used by social media to keep users engaged.
How Social Media Platforms Can Fix This
A new report by The German Marshall Fund takes the problem of disinformation head on and outlines what social media platforms can do to combat the problem and foster reliable and accurate reporting. Here are just a few of the steps the report recommends:
Design With “Light Patterns”
Websites and social media platforms often use “dark pattern” interfaces and defaults to manipulate users and hide information about how the site operates. Light pattern design, therefore, involves transparency about how the site operates. This involves using defaults that favor transparence, and even using labeling to shows the source of information, whether the account posting the content is verified or not, and even if audio and visual content has been altered.
Consistent Enforcement of Terms of Use
While all social media platforms have in-depth rules for user activity, these terms are generally inconsistently applied and enforced. By setting a transparent standard and consistently enforcing that standard, social media platforms can more successfully combat disinformation and other toxic online activity.
Independent Accountability
Instead of using government policy to regulate content, the U.S. should set up a technology-neutral agency to hold platforms accountable for a code of conduct focused on practices such as light pattern designs. By focusing on overseeing positive platform practices, the government can avoid having a hand in decisions about what content is “good” or “bad.”
What You Can Do Now
However helpful these changes to social media platforms are, the truth is we aren’t there yet. Fake and fiction stand side by side online, with no immediate way to discern which is which. When taking in information, it is up to you to figure out what is reputable and what is inaccurate. With the large amount of COVID-19 disinformation swarming the internet, its more important than ever to use our critical skills in two specific ways.
Be Self-Critical
Our personal world views, biases, and emotions shape how we take in information. When looking at content online, it’s important to think about your own motivations for believing something to be true or not. Ask yourself why you think something is true or false. Is it largely because you want to believe it or disbelieve it? When we read something online that makes us angry, there is something satisfying about sharing that anger with others. Before sharing content, ask whether your desire to share it is an emotional response or because the information is accurate and important. If it’s predominately coming from your emotions, reconsider if it’s worth sharing.
Be Critical of All Content
In general, we should initially read everything with a degree of skepticism. Doubt everything and be your own fact checker. Look at other websites reporting the same information. Are any of them reliable? Are they all citing the same sources, and, if so, is that source reputable? Don’t share an article based solely on the headline. Read the full article to understand if the headline is based on fact or is just speculation. Look at what sort of language the article is using. Is it largely opinion based? Does it cite reputable sources? Is it written in a way that is meant to evoke an emotional response?
Months into the COVID-19 pandemic, we understand how our in-person interactions can have a negative impact on ourselves and those around us, but it’s important to also understand how our interactions online can lead to similar outcomes. Given the stupefying amount of disinformation about the coronavirus circulating online, it’s more important now than ever to be think critically about what information you’re consuming and be aware about what you say and share online.
by Doug Kreitzberg | Apr 30, 2020 | Coronavirus, Cybersecurity, Human Factor
Your organization’s cybersecurity team is on edge in the best of times. The bad guys are always out there and, like offensive lineman in American Football who are only noticed when they commit a penalty, cybersecurity personal are usually noticed only when something goes wrong. Now, as the game has changed, the quick transition to work from home, combined with the plethora of COVID-19 scams, phishing, and malware drowning the cybersecurity threat intel sources—not to mention the isolation—may leave your team at a chronically high stress level. And cybersecurity is far more than just your technical safeguards. At the end of the day, the stress your team feels could lead them to put their focus in the wrong place and let their guard down.
Here’s what you can do about it
- Incorporate cybersecurity as a part of your overall business strategy process – now is the time to recognize cybersecurity as a key part of the organization’s strategy and that enables you to drive your mission forward.
- Be a part of the cybersecurity planning process – be active, listen, and understand how your team is handling this.
- Leverage your bully pulpit – communicate to the staff about the key areas your cybersecurity team is focused on and the role they are playing to keep the organization secure while everyone is working from home.
- Check in – take the time to just check in and see how they are doing. A little goes a long way.
The truth is, when it comes to cybersecurity, your first and most effective line of defense is not your firewall or encryption protocol. It’s the people that form a team dedicated to protecting your organization. Working from home poses unique cybersecurity challenges, and it’s up to you to make sure your team is given the attention they need to do their job well.