
by Doug Kreitzberg | Sep 9, 2020 | Cyber Awareness, GDPR, ransomware
In July, we wrote about a ransomware attack suffered by the cloud computing provider Blackbaud that led to the potential exposure of personal information entrusted to Blackbaud by hundreds of non-profits, health care organizations, and educational institutions. At the time the ransomware attack was announced, security experts questioned Blackbaud’s response to the breach. Now, the Blackbaud ransomware attack isn’t just raising eyebrows, with the company facing a class action lawsuit for their handling of the attack.
Blackbaud was initially attacked on February 7th of this year. However, according to the company, they did not discover the issue until mid-May. While the time it took the company to detect the intrusion was long, it is increasingly common for threats to go undetected for long periods of time. What really gave security experts pause is how Blackbaud responded to the incident after detecting it.
The company was able to block the hacker’s access to their networks, but attempts to regain control continued until June 3rd. The problem, however, was that the hackers had already stolen data sets from Blackbaud and demanded a bitcoin payment before destroying the information. Blackbaud remained in communication with the the attackers until at least June 18th, when the company payed the ransom. Of course, many experts questioned Blackbaud’s decision to pay given that there is no way to guarantee the attackers kept their word. And, to make matters worse, the company did not public announce the incident to the hundreds of non-profits that use their service until July 16th — nearly two months after initially discovering the incident.
Each aspect of Blackbaud’s response to the ransomware attack is now a part of a class action lawsuit filed against the company by a U.S. resident on August 12th. The main argument of the lawsuit claims that Blackbaud did not have sufficient safeguards in place to protect the private information that the company “managed, maintained, and secured,” and that Blackbaud should cover the costs of credit and identity theft monitoring for those affected. The lawsuit also alleges that Blackbaud failed to provide “timely and adequate notice” of the incident. Finally, regarding Blackbaud’s payment of the ransomware demand, the lawsuit argues that the company “cannot reasonably rely on the word of data thieves or ‘certificate of destruction’ issued by those same thieves, that the copied subset of any Private Information was destroyed.”
Despite the agreement among privacy experts that Blackbaud’s response to the attack was anything but perfect, lawsuits pertaining to data breaches have historically had a low success rate in the U.S.. According to an attorney involved in the case, showing harm requires proving a financial loss rather than relying on the more abstract harm caused by a breach of privacy: “The fact that we don’t assign a dollar value to privacy [means] we don’t value privacy.”
Whatever the result of the lawsuit, questions still persist on whether Blackbaud’s response violates the E.U.’s General Data Protection Regulation. The GDPR requires organizations to submit notification of a breach within 72 of discovery. Because many of Blackbaud’s clients are UK-based and the company took months to notify those affected, it is possible Blackbaud could recevie hefty fines for their response to the attack. A spokesperson for the UK’s Information Commissioner’s Office told the BBC that the office is making enquiries into the incident.
As for the non-profits, healthcare organizations, and educational institutes that were affected by the breach? They have had to scramble to submit notifications to their donors and stakeholders that their data may have been compromised. Non-profits in particular rely on their reputations to keep donations coming in. While these organizations were not directly responsible for the breach, this incident highlights the need to carefully review third-party vendors’ security policy and to create a written security agreement with all vendors before using those services.

by Doug Kreitzberg | Sep 2, 2020 | Cybersecurity, Risk Management
You can’t protect your network from an attack or a breach if you don’t know where you are vulnerable. Some vulnerabilities are easy to see, like application patching, but others can be very difficult to spot if you don’t know exactly what you are looking for. Luckily, a piece of automation software called vulnerability scanning can help organizations detect and manage vulnerabilities across an entire network.
The scan works by first creating an inventory of servers, applications, devices, firewalls, operating systems, and anything else you include within the perimeters. The scan may also attempt to login to the network using default credentials. After completing an inventory, the scan will then cross check every item detected against a database and give a full list of known vulnerabilities.
By conducting regular vulnerability scans and including the information from those scans in a cybersecurity risk assessment, you’ll not only keep your networks more secure, but can also help reduce the cost of a breach should one ever happen. Here is a short overview of how to properly conduct a vulnerability scan and use it as a key tool for more effective risk assessments.
What to Include in Your Vulnerability Scan
When conducting a vulnerability scan, it’s important to set a scope that is appropriate for your business needs and network configuration. While every organizations should scan their entire network — along with external systems, vendor portals, and cloud services — it might be preferable to run more focused scans frequently and conduct a more expansive scan every quarter or twice a year.
Some scans can also run automatically when changes to the network are made or a new device is added. Because these scans can be intrusive, it’s possible they may cause temporary systems errors. You should also consider conducting scans after business hours or at a time when essential business operations will not be affected.
Putting Vulnerabilities into Context
The unfortunate reality is that organizations will always have some vulnerabilities. Vulnerability scans are the first part in a larger process that allows you to pinpoint your weak points and prioritize these vulnerabilities based on risk. It’s important to remember that vulnerabilities are separate from threats. A cybersecurity threat is a method of attack that exploits vulnerabilities. And fixing every single vulnerability is sort of like trying to plug a hundred of holes in a bucket all at once.
A risk assessment is therefore essential for putting your vulnerability scans into context and understanding where you need to focus your energy. When looking at a list of known vulnerabilities within your network, consider how much damage it would cause if the vulnerability is exploiting, assess the threat landscape to understand how likely an attack is, and explore what security controls are needed to fix the vulnerability. If a known vulnerability is easy to fix but would be costly if exploited, you will want to address that immediately. On the other hand, if a vulnerability would require a lot of time and money to fix, and the risk of an attack is very low, you may not need to focus on that right away. No matter what, the key is to have enough information on hand to make an informed decision on how best to protect or network and systems.

by Doug Kreitzberg | Aug 31, 2020 | Cyber Awareness
When it comes to cybersecurity training, it’s easy to focus your energy on employees who may not have an advanced understanding of your network and technological systems. And, of course, it is vitally important these employees understand the basics of cybersecurity and adopt behaviors that help protect your systems from compromise. However, implicit in this way of thinking is that your IT staff, who are incredibly knowledgable about your systems, don’t need to be trained in cybersecurity. This couldn’t be further from the truth.
While your IT team is likely more aware of existing cyber threats, they also likely have administrative access across your entire network, making their account far more costly if compromised. What’s more, IBM’s 2020 Cost of a Data Breach Report found that 19% of all malicious attacks are initially caused by cloud misconfigurations, which is generally the responsibility of IT staff.
It is therefore vitally important to ensure your IT team is receiving role-specific cybersecurity training alongside the rest of your staff. This training should still cover a lot of the basics that every employee needs to know, but it should also include more specific and in-depth training in topics such as cloud configurations, access management and monitoring, network segmentation, and vulnerability scans. Your entire IT staff doesn’t need to be security experts, but everyone should have a good understanding of the current threat landscape and know how to spot any suspicious activity within your systems.
And, like all cybersecurity training, it’s important to use a program that focuses on helping your team build better, more secure habits, rather than simply throwing information at them. An important aspect of this is to simply make it easier for your IT team to do the job they need to do and do it securely. Because IT departments have highly specialized knowledge, it can be easy for business leadership to simply leave them to do what they think makes sense. However, executives should be actively involved in giving immediate feedback and listening to what IT staff need to make sure they can do their jobs efficiently and safely.
by Doug Kreitzberg | Aug 28, 2020 | Business Email Compromise, Cybersecurity, social engineering
Last week we wrote about the significant cost of business email compromise (BEC) scams compared to other, more-publicized cyber attacks. Now, the cybersecurity firm Agari has published a report showing a new BEC threat emerging — one that is more sophisticated and more costly than what we have seen in the past.
Business email compromise threats are a form of social engineering scams that have been around for a long time. “Nigerian prince scams,” for example, are what people often think of when they think of these types of attacks. However, as technology and modes of communication have gotten more sophisticated, so too have the scammers. Agari’s new report details the firm’s research on a new gang of BEC scammers based in Russia that call themselves “Cosmic Lynx.”
Unlike most BEC scams that tend to target smaller, more vulnerable organizations, the group behind Cosmic Lynx tends to go after gigantic corporations — most of which are Fortune 500 or Global 2000 companies. While larger organizations are more likely to have more sophisticated cybersecurity protocols in place, that doesn’t mean they can’t be tricked, and the payout for successful scams is significantly larger. The average amount requested through BEC is typically $55,000. Cosmic Lynx, on the other hand, requests $1.27 million on average.
How Does it Work?
While the basic’s of Cosmic Lynx’s BEC attacks are pretty standard, the group uses more advanced technology and social engineering tactics to make their scams more successful.
Typically, Cosmic Lynx uses a “dual impersonation scheme” that mimics indidvuals both within and outside of the target of the scams. Moreover, by manipulating standard email authentication settings and registering domains that imitate common secure email domains (such as secure-mail-gateway[.]cc), the group is able to convincingly spoof their email address and display name to look almost identical to a employees within the targeted business. Acting as the CEO, the group will typically send an email to a Vice President or Managing Director notifying them of a new acquisition and referring the employee to an external legal team to finalize the deal and transfer funds.
Cosmic Lynx will then impersonate the identity of a real lawyer and send the employee an email explaining they are helping to facilitate the payment. Of course, organization receiving the funds is actually a mule account — typically Hong Kong-based — controlled by Cosmic Lynx.
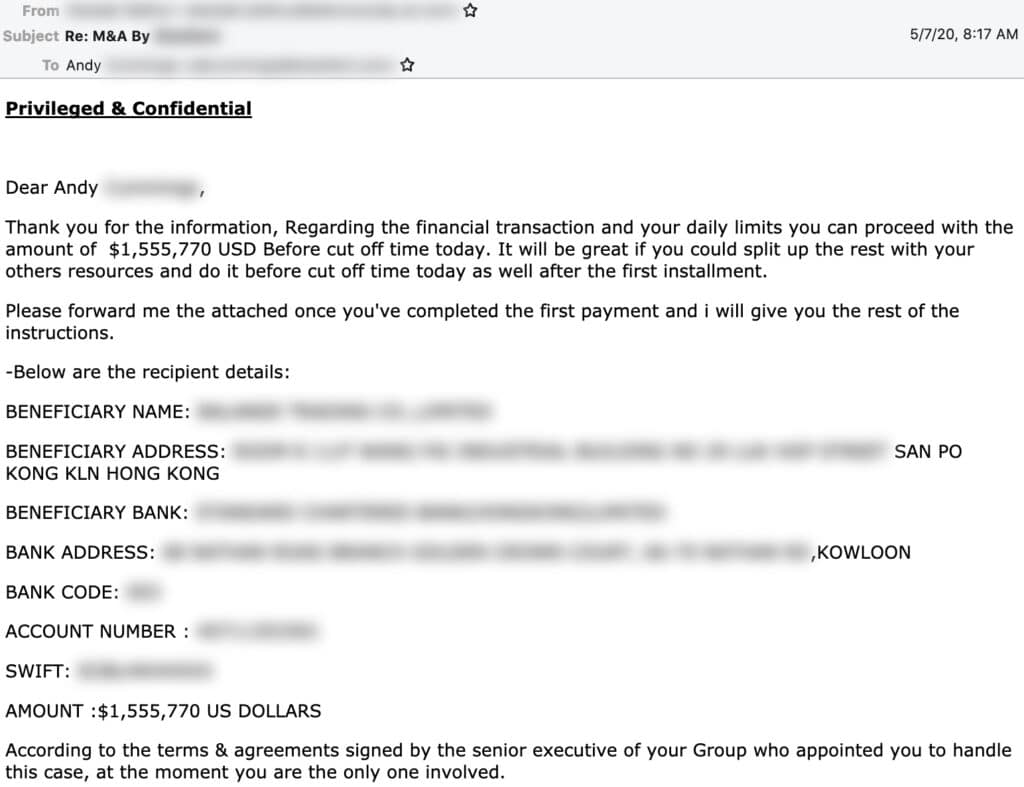
Source: Agari
For now, Cosmic Lynx seems to be the only group carrying this new BEC threat, however it is very likely other groups, seeing the amount Cosmic Lynx is raking in, will begin to follow suit. Simply put, the level of sophistication involved in these scams will require businesses to have more sophisticated protections in place to prevent this new threat. While more advanced email filters may help to detect spoofed email addresses, the most effective method to prevent BEC scams is to have strong policies in place to verify payment requests before releasing funds.
by Doug Kreitzberg | Aug 26, 2020 | Cybersecurity, Identity
When we think about cybersecurity, we usually think about it in terms of an inside and an outside. You have your network, application, and data all instead one system, and cybersecurity is about keeping the bad guys on the outside. For awhile, this “castle and moat” model of cybersecurity made a lot of sense. However, as technology has advanced and business needs have changed, experts are now shifting towards a new way of thinking about cybersecurity: zero trust.
The problem with the traditional approach to cybersecurity is that the lines between inside and outside are now blurred. Instead of keeping all our applications and data in a central location, the introduction of cloud-based services has spread out our network into multiple locations with multiple points of access. What’s more, with the recent rise in remote work, our networks are less centralized than ever before.
In many ways, hackers have understood the implications of these changes far faster than we have. Today, brute force attacks have taken a backseat to credential compromise, phishing, and other attacks that allow bad actors to gain access by using your network settings rather than breaking them. And if you use the traditional cybersecurity model, once a hacker gains access to your network, they can spend months freely moving around your network before launching an attack.
That’s why cybersecurity experts are pushing what is called “zero trust” cybersecurity. In essence, this strategy involves verifying the identity and access needs of every single user — no matter if they are coming from inside or outside your network. Instead of assuming that it’s okay to trust anyone already in your network, zero trust means everyone should be mistrusted until proven to be legitimate.
One aspect of zero trust involves using technology to secure your network from the inside out. Multi-factor authentication, network segmentation, and identity and access management systems are all key tools for a zero trust security posture. It’s important to keep a close watch on the access employees have to move around your network. Best zero trust practice means only giving access to an employee for specific business needs then revoking that access after a fixed period of time. Using these practices can help protect your network if an employee’s credentials are compromised.
While using cybersecurity technology will help you build towards a zero trust framework, without proper governance structures and an overall zero trust culture your organization will remain vulnerable. It’s essential that business leadership understands the concept of zero trust and are active in crafting a culture that values this model of security. If an employee receives an invoice from a vendor, for example, it should be standard procedure to verify the identity of the vendor and the payment request before releasing funds.
At the end of the day, a zero trust approach to cybersecurity requires an active and ongoing effort to prevent cyber threats. Security technology, policies, and culture should be built into your business strategy by design rather than retroactively applied.

by Doug Kreitzberg | Aug 24, 2020 | Business Email Compromise, ransomware, Risk Management
According to this year’s Cost of a Data Breach Report, the majority of malicious cyber attacks are financially motivated. So, when prioritizing risk, it makes sense to focus on cyber threats that have direct financial implications, such as ransomware and business email compromise (BEC) schemes.
Given the recent rise in ransomware attacks and the targeting of public agencies, it’s pretty likely you’ve seen some news about ransomware within the past year. And while it is certainly important to protect against the possibility of ransomware, that doesn’t mean less-publicized cyber attacks like BEC should be taken any less seriously.
In general, business email compromise involves scammers sending employees an email that looks as if it is coming from a familiar source requesting some sort of payment. Usually, scammers will impersonate frequently used vendors or even CEOs. And these scams can be costly. Last year Nikkei, a Japanese media company, suffered a loss of $29 million when a scammer impersonated a company executive.
In fact, BEC scams have repeated topped the FBI’s annual Internet Crime Report as the costliest form of cyber crime. And, when you compare the costs of BEC and ransomware attacks, it becomes pretty clear which one poses the greater risk.
[table id=1 /]
While FBI’s report shows a sharp increase in ransomware losses in recent years, BEC scams continue to outpace ransomware by a staggering margin. If you were responsible for prioritizing risk activities in your organization, where would you focus? When you follow the money, the answer is pretty obvious. The good news, however, is that a lot of the procedures, guidelines, and training that can be done to prevent BEC can also help ransomware, such as anti-malware software and email authentication. It can be easy to base your cybersecurity processes off of what you see in the headlines, but that won’t always give you an accurate view of your risk profile. It’s essential to conduct regular risk assessments to gain a clear understanding of the biggest threats your organization faces.

by Doug Kreitzberg | Aug 21, 2020 | Risk Culture
When we think of risk — especially in cybersecurity — we usually think about the things we do that can hurt us: clicking on that phish, accidentally forwarding an email to the wrong party, wiring money to the wrong (or fraudulent) bank account.
However, we should also pay attention to what we don’t do, such as failing to patch the system as soon as an update is available, failing to act on findings in a vulnerability scan, failing to change or strengthen our passwords, failing to add multi-factor authentication, or failing to review logs. Sometimes, our ability to accept “passive risk,” such as putting off taking an action to another day can be more pernicious than active risk. In fact, misconfigurations — a form of passive risk — is a top threat factor, according to Verizon’s 2020 Data Breach Investigations Report.
A recent paper describes a series of studies conducted that assess employees’ level of passive risk. According to the results, those that stated that their tolerance for passive risk was high also exhibited those passive risk cybersecurity behaviors. Interestingly, however, the study did not find the same correlation between active risk assessments and active risk behaviors.
So, how can you address passive risk? Design the behaviors that you would like to see and test changes in processes with the staff that seems most prevalent to passive risk. One example is to facilitate the automation of patching so that it makes it easy for the IT staff to perform. Another option is to take the time to fine tune log alerts so that the team does not have to deal with a lot of false positives. The paper also suggests changing the wording of certain security features to highlight the consequence of passive risk behavior. For example, instead of referring to passwords as “strong” or “weak,” using phrases such as “low risk” or “high risk” passwords can help drive home the potential consequence of poor credential management.
Whatever methods you use, In today’s remote environment, it’s always important to take the time to get together with your team and bond with them. Having a better relationship with your team can help generate the cohesion that is necessary for a risk-aware culture.

by Doug Kreitzberg | Aug 19, 2020 | Artificial Intelligence, Disinformation, Human Factor, Phishing, social engineering
Earlier this month, a study by the University College London identified the top 20 security issues and crimes likely to be carried out with the use of artificial intelligence in the near future. Experts then ranked the list of future AI crimes by the potential risk associated with each crime. While some of the crimes are what you might expect to see in a movie — such as autonomous drone attacks or using driverless cars as a weapon — it turns out 4 out of the 6 crimes that are of highest concern are less glamorous, and instead focused on exploiting human vulnerabilities and bias’.
Here are the top 4 human-factored AI threats:
Deepfakes
The ability for AI to fabricate visual and audio evidence, commonly called deepfakes, is the overall most concerning threat. The study warns that the use of deepfakes will “exploit people’s implicit trust in these media.” The concern is not only related to the use of AI to impersonate public figures, but also the ability to use deepfakes to trick individuals into transferring funds or handing over access to secure systems or sensitive information.
Scalable Spear-Phishing
Other high-risk, human-factored AI threats include scalable spear-phishing attacks. At the moment, phishing emails targeting specific individuals requires time and energy to learn the victims interests and habits. However, AI can expedite this process by rapidly pulling information from social media or impersonating trusted third parties. AI can therefore make spear-phishing more likely to succeed and far easier to deploy on a mass scale.
Mass Blackmail
Similarly, the study warns that AI can be used to harvest a mass information about individuals, identify those most vulnerable to blackmail, then send tailor-crafted threats to each victim. These large-scale blackmail schemes can also use deepfake technology to create fake evidence against those being blackmailed.
Disinformation
Lastly, the study highlights the risk of using AI to author highly convincing disinformation and fake news. Experts warn that AI will be able to learn what type of content will have the highest impact, and generate different versions of one article to be publish by variety of (fake) sources. This tactic can help disinformation spread even faster and make the it seem more believable. Disinformation has already been used to manipulate political events such as elections, and experts fear the scale and believability of AI-generated fake news will only increase the impact disinformation will have in the future.
The results of the study underscore the need to develop systems to identify AI-generated images and communications. However, that might not be enough. According to the study, when it comes to spotting deepfakes, “[c]hanges in citizen behaviour might [ ] be the only effective defence.” With the majority of the highest risk crimes being human-factored threats, focusing on our own ability to understand ourselves and developing behaviors that give us the space to reflect before we react may therefore become to most important tool we have against these threats.
by Doug Kreitzberg | Aug 17, 2020 | Business Email Compromise, Cyber Awareness, Phishing
We understand the risks of having our email credentials compromised. If it happens, we know to change our login information as quickly as possible to ensure whoever got in can’t continue to access our emails. The problem, however, is that there is a very simple way for hackers to continue to access the content of your inbox even after you change your password: auto-forwarding. If someone gains access to your email, they can quickly change your configurations to have every single email sent to your inbox forwarded to the hacker’s personal account as well.
The most immediate concern with unauthorized auto-forwarding is the ability for a hacker to view and steal any sensitive or proprietary information sent to your inbox. However the risks associated with this form of attack have far greater ramifications. By setting up auto-forwarding, phishers can carry out reconnaissance efforts in order to carry out more sophisticated social engineering scams in the long-term.
For example, auto-forwarding can help hackers carry out spear phishing attacks — a form of phishing where the scammer tailors phishing emails to target specific individuals. By learning how the target communicates with others and what type of email they are most likely to respond to, hackers can create far more convincing phish and increase the chance that their attack will be a success.
Bad actors can also utilize auto-forwarding to craft highly-sophisticated business email compromise (BEC) attacks. BEC is a form of social engineering in which a scammer impersonates vendors or bosses in order to trick employees into transfering funds to the wrong place. If the scammer is using auto-forward, they may be able to see specific details about projects or services being carried out and gain a better sense of the formatting, tone, and style of invoices or transfer requests This can then be used to create fake invoices for actual services that require payment.
How to protect yourself from unauthorized auto-forwarding
There are, however, a number of steps you and your organizations can take to prevent hackers from setting up auto-forwarding. The most obvious is to prevent access to your email account in the first place. Multi-factor authentication, for example, places an extra line of defense between the hacker and your inbox. However, every organization should also disable or limit users’ ability to set up auto-forwarding. Some email providers allow organizations to block auto-forward by default. Your IT or security team can then manually enable auto-forwarding for specific employee’s when requested for legitimate reasons and for a defined time period.
When it comes to the risks with auto-fowarding, the point is that the more the hackers can learn about your organizations and your employees, the more convincing their future phishing and BEC attacks will be. By putting safeguards in place that help prevent access to email accounts and block auto-forwarding, you can lower the risk that a bad actor will gain information about your organization and carry out sophisticated social engineering attacks.

by Doug Kreitzberg | Aug 14, 2020 | Behavior, Cybersecurity
We’ve talked about the human factors of cybersecurity and the importance of exposing employees to social engineering scams and other attacks that exploit human vulnerabilities. However, when we look at how to improve our organization’s digital practices, we have to do more than train and simulate phish. We have to take a look at what we are asking staff to do and make sure that the cybersecurity behaviors we want them to do are easy, not difficult. Otherwise, those behaviors will become hard to sustain in the long term.
When you’re trying to create new behaviors — for yourself or for your employees — it’s essential to remember that motivation is not a constant. You might be energized and excited to spot phishing emails when you first learn about it, but overtime that could fade. You might get stressed about other parts of your job, or you might be distracted by friends and family, and overtime your interest in your new habit may start to fade. But that is okay! According to behavior scientist BJ Fogg, instead of trying to keep yourself motivated, focus on creating behaviors that are so easy you can do them without worrying about motivation at all.
So, when it comes to fostering cybersecurity behaviors in your employees, it’s essential to keep things short and easy to do. And the truth is, there are a number of super easy cybersecurity behaviors that will help keep you, your employees, and your businesses from being vulnerable to cyber threats. Here are just a few:
Automated Security Scanning
One example of a simple behavior for your software security is to run applications through an automated security scanning tool. Automation is becoming more and more helpful for relieving some of the burden off your IT and security staff. Now, many scanning tools can be set to run automatically, and will highlight potential vulnerabilities with your applications, systems, and even websites. This will leave your security team to evaluate and patch vulnerabilities, instead of wade through your entire system looking for any holes.
Single Sign-On
Another important and easy cybersecurity tool is single sign-on (SSO). Essentially, SSO allows employees to use one set of credentials to access a variety of separate services and applications. While it may seem safer to have different credentials for every applications, single sign-on can actually create stronger authentication processes across the enterprise. As companies began to rely on more and more services, each requiring different credentials, it became hard for employees to keep track of all their log in information, leading to worse password hygiene. By combining all credentials into one, it is easier for employees to use smart and secure credentials.
Phish Reporting
One other easy cybersecurity behavior you can implement is a phish reporting button within your email provider. It’s essential that your IT department is aware of any phishing emails being sent around the office, and in many cases it’s up to the employees to report any phish they receive. While simply forwarding an email to your IT help desk might not seem like a lot, using a simple button to report potential phish is that much easier. Implementing a feature as simple as a report button can increase your reporting and help your IT department keep the network safe.
There are plenty of additional cybersecurity behaviors that you can make easy. All you have to do is first look at what people do, find out what is making the behaviors you want to see difficult to accomplish, then work to make them easier.










